How to Fill Out a Cyber Security Insurance Application For Lower Rates
Cyber attacks targeting local and regional businesses are hitting an all time high. While Small and Midsize Businesses (SMBs) can benefit from cyber insurance, the cost of cyber insurance premiums is often a pain point—leaving SMBs vulnerable. Here are the basics when it comes to cyber liability insurance and how to optimize premiums and coverage.
Cyber attacks are no longer an ambiguous incident that only big corporations need to consider—they are an active threat to all organizations, including small to mid-sized businesses. SMBs can actually suffer greater repercussions from IT and data breaches since they often cannot cover the subsequent damage expenses. The cost of an incident, include downtime and loss of production, loss of customer trust, and (far too often) ransoms or lawsuits.
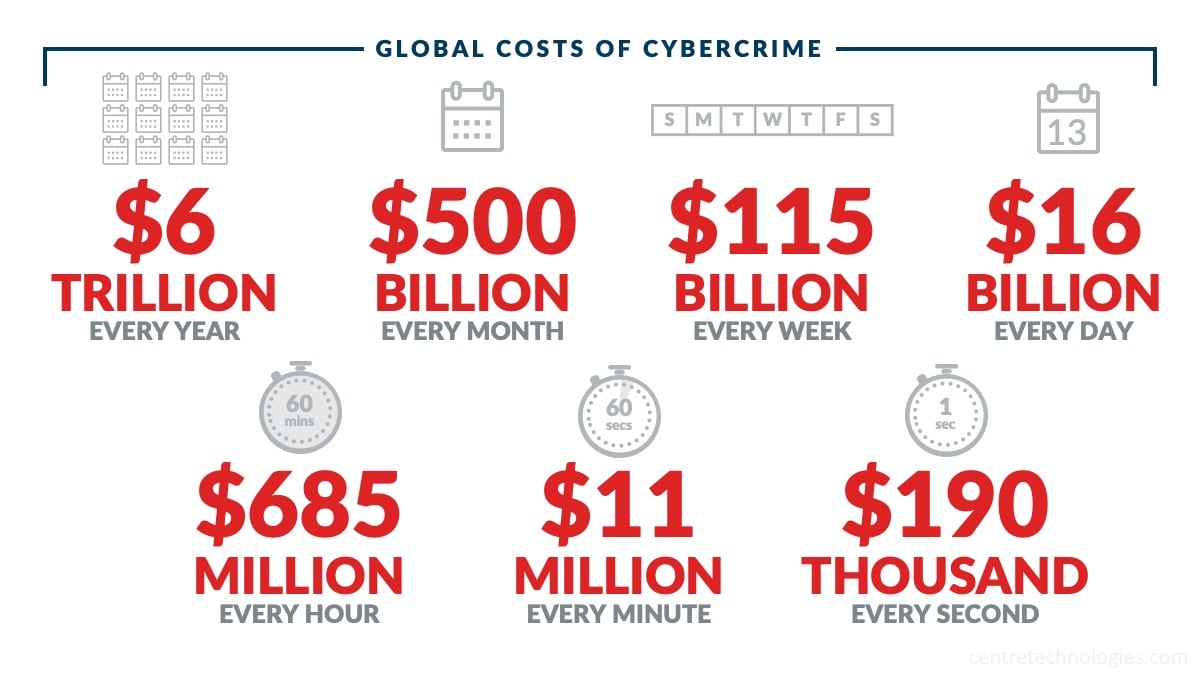
In fact, if measured as its own country, the dollar amount of damages from cybercrime would make it the third-largest economy in the world, coming in at a whopping $6 trillion dollars!
Cyber security insurance, also known as cyber liability insurance, is becoming a necessity for businesses to manage IT risk in the event of a cyber security incident. Like all insurance policies, rates, limits, and coverage an organization receives varies greatly and is based on potential risks and losses. Through proper security tools and hygiene, businesses can prepare themselves to qualify for lower premiums and better coverage during the insurance application process.
What factors affect cyber insurance Rates?
Organizations obtaining cybersecurity insurance policies will have to fill out an application with an insurance broker, including a questionnaire asking about their current IT security environment. The answers provided are then used to determine a business's eligibility, potential risks, and rates for a given insurance policy.
Read below to discover some of the key IT security topics and areas assessed in cyber insurance applications and questionnaires, and steps that can be taken for a better insurance policy, including lower premiums and higher payout limits.
Employee Security Awareness
Over 47% of business leaders have reported that human error has been the cause of a data breach at their organization. Employee security awareness training attempts to combat employee negligence and poor security practices, such as reusing passwords or clicking on unknown links, through a collection of educational courses, content and assessments.
Cyber insurance brokers ask businesses if they have a security awareness program in place because brokers know that such programs can help prevent cyber attacks at the source and reduce damages. They may also assess your rate and coverage based on whether your organization performs routine threat and phishing simulation exercises to prevent ransomware incidents.
Organizations can buy these cybersecurity programs and services from a variety of information security companies. Partnering with an IT company can be helpful in ensuring your business uses a trusted security awareness training program, aid in tailoring the content to your business operations and needs, as well as manage and report adoption throughout your organization. An IT provider can also help implement and schedule recurring objective and effective simulations and phishing exercises.
Email Systems Security
 Email servers are one of the most common ways malicious actors penetrate IT systems and networks. Cyber security insurance brokers may reduce premiums or increase coverage if an organization has proper security applications, tools, and configurations in place to alert IT administrators of security threats before expensive harm or damages occur.
Email servers are one of the most common ways malicious actors penetrate IT systems and networks. Cyber security insurance brokers may reduce premiums or increase coverage if an organization has proper security applications, tools, and configurations in place to alert IT administrators of security threats before expensive harm or damages occur.
Businesses should carefully research the specs, capabilities, and settings of their current email servers as well as perform recurring vulnerability scans and penetration testing. They may need to invest in newer applications and email clients, such as Microsoft Outlook 365, that provide advanced email security features and alerts users when an email is suspicious or comes from outside of the organization.
Protective DNS (PDNS)
A protective DNS service (PDNS) analyzes DNS queries to identify and mitigate threats, by checking queries and IP addresses against threat intelligence. The PDNS then prevents connections to suspicious sites, reducing ransomware, malware, phishing attacks, and access to malicious actors.
Cyber insurers may ask whether the business is using DNS filtering and geofencing security tools, like those included with Secure Managed Services, with optimal implementation and configurations. These cybersecurity protections help reduce the IT security vulnerabilities of a business.
Multi-Factor Authentication Configurations
Multi-Factor Authentication (MFA) helps your network, device, or software application confirm the identity of a user trying to log-in. MFA not only helps prevent malicious and unknown actors from entering your IT systems, but also alerts you when attempts do occur. This level of visibility and control enables proper investigation and awareness after a potential breach.
 Some insurance brokers will not only offer a better policy to those with MFA enabled, but will often provide any coverage (or policy renewal) only if multi-factor security is configured for all user accounts and/or remote connections.
Some insurance brokers will not only offer a better policy to those with MFA enabled, but will often provide any coverage (or policy renewal) only if multi-factor security is configured for all user accounts and/or remote connections.
Organizations may be able to manually configure their devices to enable MFA, but adoption rates are often times low. Some businesses may even have to switch to newer technologies that have this feature. Many organizations see higher adoption rates when engaging with an IT provider to managed MFA deployment as part of Secure Managed Services.
Data Backups Storage and Process
With data becoming an increasingly valuable IT assets for all organizations, data protection becomes one of the biggest priorities during a cyber incident. Therefore, cyber insurers are often focused on the security, isolation, and routine assessment of data backups and backup process.
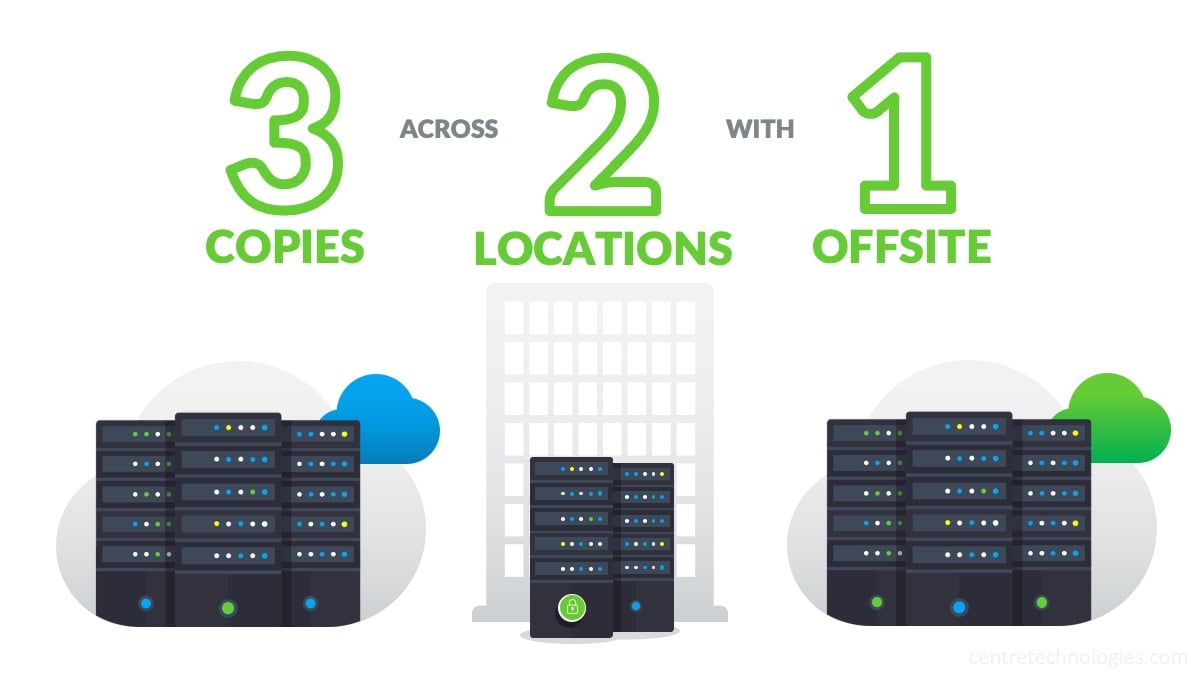
Although there are many methods, products, and services business can utilize to backup their data, not all Backup and Disaster Recovery solutions are created equal. Most organizations benefit from some sort of automatic or managed backup routine that ensures even the most recent data is verified, encrypted, and protected. Businesses also need to consider how many backups to have and where. Centre’s IT consultants recommend the industry best practice of the 3-2-1 model—3 copies across 2 locations with 1 offsite or locked (aka. immutable).
Advanced Threat Hunting and Response Tools
The technology to help combat cyber incidents and subsequent damage, including malware and ransomware, is rapidly advancing. Insurers look at whether an organization is utilizing the latest cybersecurity protections and tools that use sophisticated hardware and software to detect and respond to cyber threats.
These technologies may include, Next-Generation Anti-Virus (NGAV) and Endpoint Detection and Response (EDR). NGAV goes beyond traditional anti-virus by including artificial intelligence (AI), behavioral detection, machine learning, and exploit mitigation in effort to block zero-day exploits. EDR then adds another layer of cybersecurity protection, automatically containing cyber threats by quarantining compromised devices from other network devices. Businesses can buy these security tools as individual solutions or as part of Secure Managed Services. The latter may be more cost-effective, especially for SMBs experiencing or anticipating growth.
Incident Response Plan
 An Incident Response Plan (IRP), or disaster recovery plan, outlines key products, services, and strategies businesses utilize to minimize downtime, damage, and costs resulting from a disaster or cyber attack. A comprehensive IRP has many different components to promote business continuity, and different carriers of cyber insurance policies may ask about different aspects of your IRP. For example, cyber insurance focused on cyber security and ransomware may specifically ask about your business recovery plan in the case of a ransomware attack.
An Incident Response Plan (IRP), or disaster recovery plan, outlines key products, services, and strategies businesses utilize to minimize downtime, damage, and costs resulting from a disaster or cyber attack. A comprehensive IRP has many different components to promote business continuity, and different carriers of cyber insurance policies may ask about different aspects of your IRP. For example, cyber insurance focused on cyber security and ransomware may specifically ask about your business recovery plan in the case of a ransomware attack.
Businesses may qualify for lower rates or better coverage if they have a plan in place to reduce the short-term and long-term costs of a cyber attack. Organizations can hire a cybersecurity consultant, a security-focused Managed Services Provider (MSP), or Managed Security Services Provider (MSSP) for a tailored and detailed plan for swift recovery and reduced damages.
Reducing insurance premiums and qualifying for better coverage
Small to mid-sized organizations may feel that the expense of cyber insurance is too much. However, with the proper technology and practices to increase data recoverability, employee awareness, and customer protection, companies can reduce their cyber liability, and therefore their insurance premiums.
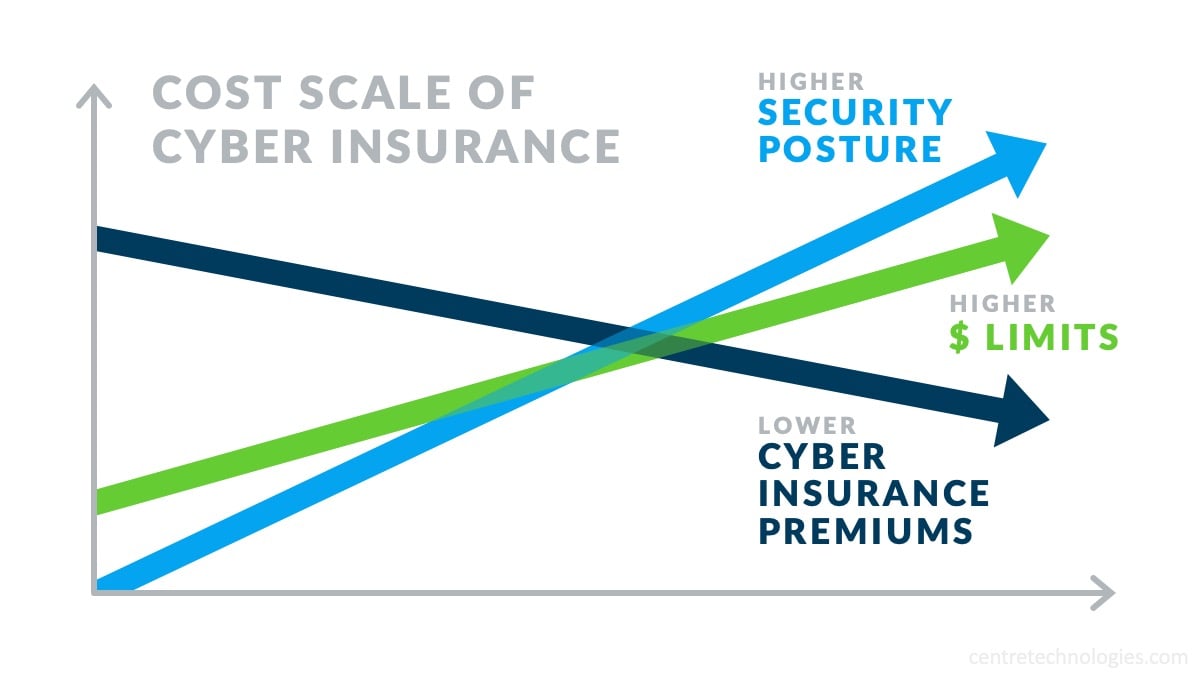
Additionally, many cyber insurance providers have conditions for their coverage, limiting or excluding benefits in certain cases where company negligence results in an incident or breach. Organizations with a rigorous and layered security environment are far less likely to fall victim to failing policy conditions, and more likely to receive funds when an incident does occur.
What to do now For better cyber liability protection
While cyber insurance is not a comprehensive solution for IT risk management and business protection, it is increasingly becoming a necessary component of every business’s incident response plan. An organization’s ability to reduce their cyber insurance premiums, or even receive coverage in the first place, depends on their current cyber security posture.
Contact Centre Technologies for help and advisory in implementing the right practices and technologies for your business to maximize its cyber insurance investment.
Be a thought leader and share:
About the Author
Organizations entrust Centre with protecting their technology ecosystem and strengthening their security posture. Centre’s cybersecurity and compliance solutions delivers layered IT security to protect businesses’ employees, customers, and content from known and unknown threats. Through employee awareness training, detailed security assessments, and 24x7 threat containment, Centre is a trusted partner for businesses seeking comprehensive network and data protection. Learn more about Cybersecurity and Compliance »


