Security in Education
We are all familiar with stories of those who have suffered from a data breach causing extreme financial burden for an organization and those affiliated. These circumstances are on the rise, ultimately validating the notion that no person or organization is safe from becoming victim.
One alarming trend is the targeting of K-12 Education organizations. Ripe for the taking, these organizations operate on limited budgets, charged with protecting the identity of their patrons that are known to have zero credit history, no workforce experience, and little to no credit monitoring in place. In other words, a clean slate for cyber criminals.
With large entities breached with almost limitless budget and resources, educational institutions have a tall order to fill in protecting our future generations against this multi-billion-dollar dark market.
Too many times we hear about breaches involving personal data- sensitive information that could financially ruin a family or close friend with disastrous results, often taking years to fully resolve. One alarming trend is the targeting of K-12 Education infrastructure.
— Enterprise Architect at Centre Technologies
Cyber criminals seek to use this information no differently than how identity theft uses Personal Identification Information (PII), any data that can be potentially used to identify a particular person. New credit lines and bank accounts, cars and home loans, filing for government services and false tax reports can all be fraudulently achieved using sensitive PII. It all adds up, and ultimately, both the child and guardian suffer as a result, including the child having a poor credit rating before they can legally work.
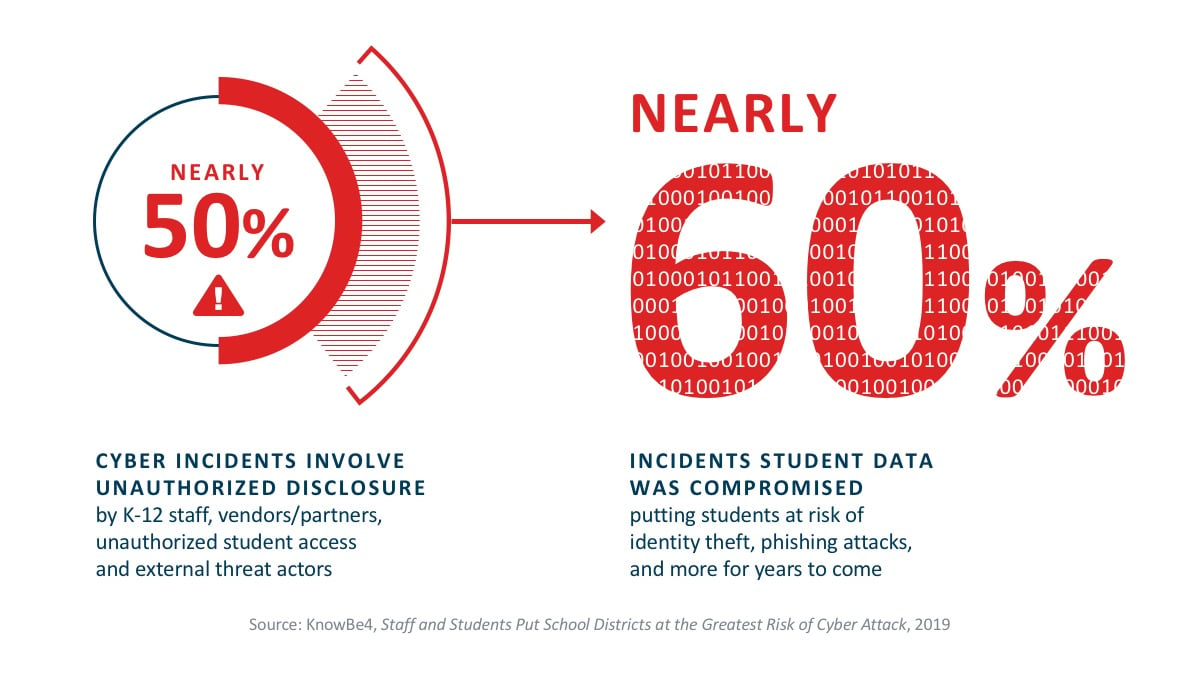
With so much at stake, how does one defend against a landscape of constant, evolving attacks? How do you plan around these new attack vectors, seemingly coming from every angle, daily?
Safe Guarding Sensitive Information
Securing sensitive personal data within any any organization can be as complex as the data at risk. While there are many ways to improve security posture by reducing vulnerabilities, organizations that are successful at protecting sensitive information in the long-term:
- Build an in-house security practice complete with a security officer and team of resources along with the addition of the right technology and policy.
- Outsource these security roles, the technology stack and policy creation to a trusted advisor.
- Take a hybrid approach and build a partnership with a trusted advisor to work through the approach in phases strategized together.
- Engage in security awareness training, including email phishing.
Each of these solutions may present various challenges such as political buy-in from leadership, amount or level of effort, shift in operational approach and budget constraints. Many times, finding a trusted advisor is half the battle—finding an advisor that also delivers "secure by default" solutions that address day-to-day managed IT, cloud compute and storage, as well as layered cybersecurity protections can offer the correct guidance to mirror your existing business needs.
Bottomline: Whomever you choose as your trusted advisor, make sure you’re taking action to aid in protecting our future generation from threats such as digital fraud, ID theft, or otherwise.
Securing Future Generations
As a guardian what can you do to ensure your child’s sensitive information isn’t misused?
- Put a freeze on your child’s credit
- Subscribe to a credit protection service
- Pull credit reports for everyone in the household yearly
- Be diligent about who you share your child’s social security number and other sensitive data with—ask questions
Additional Resources:
- Hackers' Latest Target: School Districts:
https://www.nytimes.com/2019/07/28/us/hacker-school-cybersecurity.html - Child Identity Theft is a Growing and Expensive Problem:
https://www.cnbc.com/2018/04/24/child-identity-theft-is-a-growing-and-expensive-problem.html - Child Identity Theft:
https://www.consumer.ftc.gov/articles/0040-child-identity-theft - Identity Theft:
https://en.wikipedia.org/wiki/Identity_theft

 Security in Education">
Security in Education">


