How The New TSA Cybersecurity Directive Impacts Pipeline Operations
The Transportation Security Administration's (TSA) new Cybersecurity Directive alters pipeline cybersecurity policies that have been in place for twenty years. If you've been watching the news lately, you might easily attribute this to the uptick in cyberattacks on businesses. Ransomware attacks after security breaches after payout, so many companies are impacted due to the vulnerabilities in their environment. Texas Chief Information Officer at Lotus Midstream, Brian Hoogendam, tells us more about his experience and how to equip for third-party audits in our latest webinar.
A Catalyst: The colonial pipeline cyber attack explained
The most recent cyber attack to spur government action (and one that is a direct effect of Lotus Midstream's audit) is the Colonial Pipeline cyber attack. On May 7th, 2021, the suspect ransomware group Darkside breached Colonial Pipeline. Colonial Pipeline operates out of Houston, Texas but runs nearly half of the pipeline along the East Coast of the United States. Once the breach occurred, Colonial Pipeline decided to shut down until they could obtain their data again. “A confidential assessment prepared by the Energy and Homeland Security Departments found that the country could only afford another three to five days with the Colonial pipeline shut down before buses and other mass transit would have to limit operations because of a lack of diesel fuel” (Sanger, 2021). To restore business operations, Colonial Pipeline paid nearly $5 million to hackers.
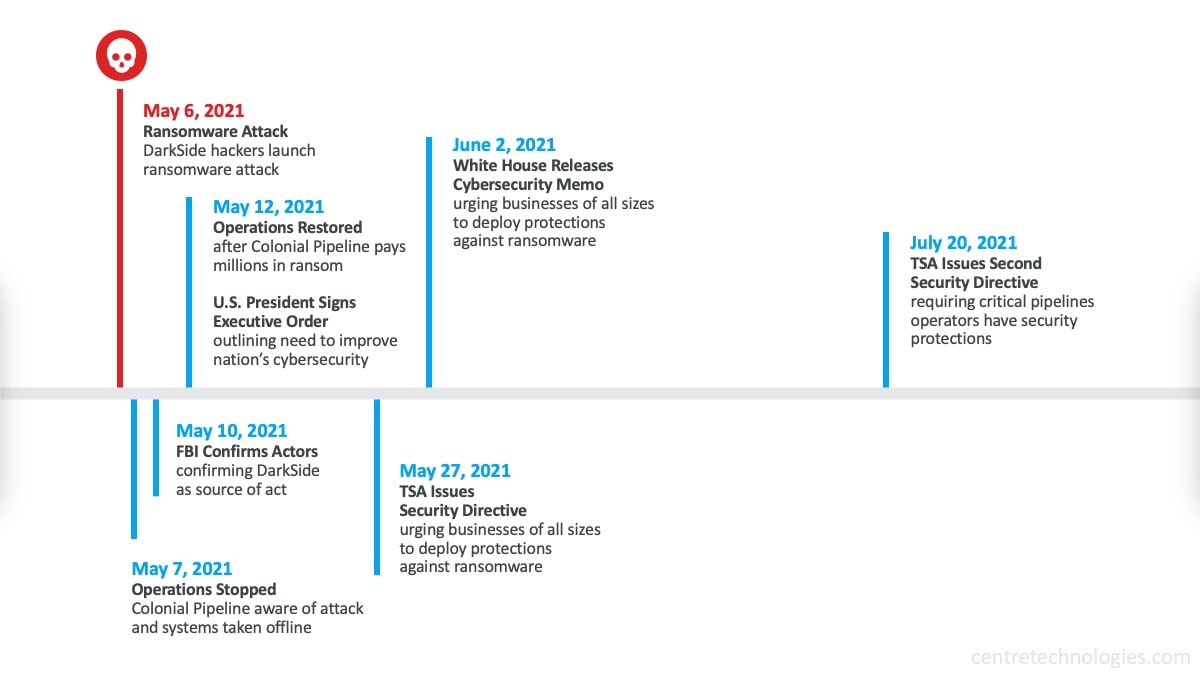
On June 2, 2021, the Federal Government released a memo directly to all business leaders urging them to immediately convene their leadership teams and evaluate ransomware threats, security gaps, corporate security posture, and business continuity plan. In a race to ensure the government and the U.S. are protected, the Department of Homeland Security (DHS) has stepped in by nominating the Transportation Security Administration (TSA) to deem certain industries and businesses critical to keeping the US economy afloat. The TSA, under the instruction of Homeland Security (DHS), started by performing IT audits on the top 150 electric utilities. Following the Colonial Pipeline attack, DHS expanded its reach to pipeline operators. Following a similar model as before, the TSA tagged the top 100 pipelines and added the IT audit to their normal annual TSA inspections. Afterward, 100 pipelines were deemed critical. This number is forecasted to expand and spread to other industries.
The reaction: The tsa pipeline security directive audit
There are two components to the TSA Pipeline Security Directive audit. First, there is a Corporate Security Review (CSR) and then security directives. The TSA utilizes the CSR as a voluntary program that companies can opt in to for review to prove they are maintaining safety standards. When the security directives came out, they mandated the CSR with a deadline for completion at the end of the calendar year. This CSR was an extremely detailed 200-part questionnaire that focused on IT security, operational security, and operations. Hoogendam’s encounter with the CSR surprised him because of the detailed requirements that the government wanted to affirm were a part of Lotus Midstream's business practices.
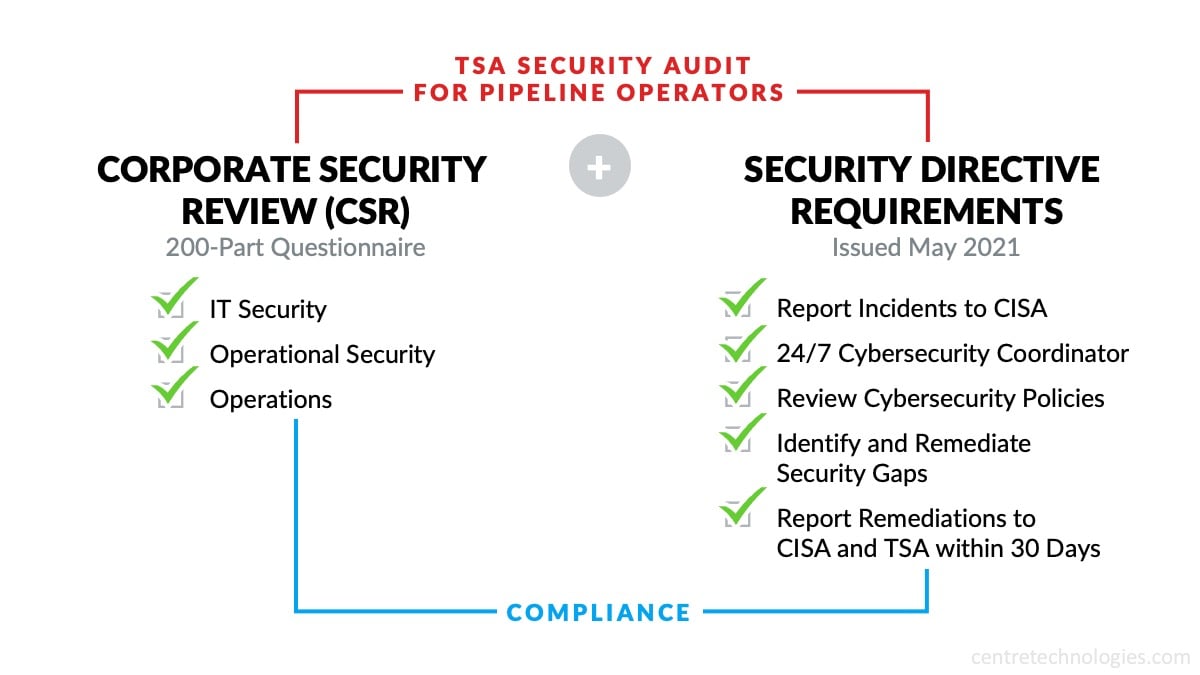
What the TSA security audit means for Pipeline Operators
Cyber Insurance is Still Important
Lately, Centre has been working through cyber insurance requirements with businesses working to obtain cyber insurance. During this process, clients are handed a long questionnaire that they need to pass. Hoogendam has gone through this process as well, and interestingly, there was not much correlation with the TSA audit. The TSA is more focused on traffic traversing networks, isolations, and segmentation whereas cyber insurance policies are focused on operation; making sure you have clean back-ups and multi-factor authentication. From Hoogendam’s experience, the cyber insurance policy seems to make more sense.

Decision Making Should Be Based on Value, not Fear
Hoogendam dives further into the concept of communicating value versus fear to leadership teams. Cybersecurity is important, and a critical piece to keeping businesses protected. When decisions need to be made to purchase new protection solutions, run a penetration (PEN) test, or a vulnerability scan. When it's time to speak to leadership, always remember to relate it back to the business.

“If we spend these dollars, we will get this result and this type of defense and this is what it means for the business.”
Brian Hoodgendam
Texas Chief Information Officer at Lotus Midstream
The Standard for the Modern CIO is Much Higher Than It Used to Be
Thanks to the new cybersecurity directive, CIO's have more requirements to meet. “It is expected that you have a clean copy of data. It is expected that you have true logging at an endpoint level. It’s expected that you’re doing multi-factor authentication. You are required to do things [differently]. Now the TSA is saying you [need] to have multi-factor authentication,” Hoogendam claimed.
“It's expected that you have a clean copy of data ...that you have true logging at an endpoint level ...that you're doing multi-factor authentication..."
Brian Hoodgendam
Texas Chief Information Officer at Lotus Midstream
Ultimately, IT is held responsible for the safety of the company. If that statement is true, they have to have a seat at the executive table and report directly to the CIO or CEO. Obtaining that level of access allows you to express your concerns across every line of business in the company. It seems hard. The best way to explain why this alignment needs to occur is that the head of IT is now having to sign off on documents the same way the CFO signs off on financial papers. If the head of IT is on the hook for the business they should report just as an officer would. Once the stakes rise, you need to take that seat. Out of sight, out of mind is no longer acceptable.
protect your business with a cyber security Assessment
“If you haven’t done a table-top exercise, a penetration test, or a threat hunt, you need to do one now,” Hoogendam exclaimed. Once you spend money on examining the vulnerabilities within your network, share the results and get them fixed. Search for integrity problems, get in the weeds and evaluate your environment for vulnerabilities. This is not to play the blame game, but to protect the business and continue operating.
Don't Forget to Utilize Partners
Industry CIOs, you need to be transparent. It's important to keep the conversation centered on value and the table stakes. Your competition is doing it and it benefits you to follow suit. With so many different options in security tools, it's best to rely on your team and do what is optimal for the business. Different groups offer different values but pulling together benefits your business in the long run.

Centre Technologies is here to consult with any of your cyber insurance questions. While cyber insurance is not a comprehensive solution for IT risk management and business protection, it is increasingly becoming a necessary component of every business’s incident response plan. An organization’s ability to reduce cyber insurance premiums, or even receive coverage in the first place, depends on its current cyber security posture.
Contact Centre Technologies for help and advisory in implementing the right practices and technologies for your business to maximize its cyber insurance investment.
About Lotus Midstream
Lotus Midstream is an independent energy company focused on developing midstream infrastructure and services necessary to transport crude oil and condensate from the wellhead to the market. Lotus owns the Centurion Pipeline System, a large-scale, integrated network of approximately 3,000 miles of crude oil gathering and transportation pipelines. Learn more about Lotus Midstream »




