7 Cyber Scams to Lookout for on Black Friday and Cyber Monday
What do businesses have in common with cyber criminals? They're both preparing to bring in the cash this Black Friday and Cyber Monday. Online spending surged by nearly 22% last year on Black Friday and it is expected to surge again this year. Cyber Monday brought in $10.8 billion just last year, which was a considerable increase from 2019's $9.4 billion. Because of the “Act Now!” mentality pushed between the two holidays, urging consumers to hurriedly take advantage of the best deals, a lot tends to slip through the cracks for consumers. By being aware of these cyber scams and how to avoid them, you can avoid being bamboozled this holiday season.
Common black Friday and Cyber Monday scams
Cyber attacks spike when there is an event that entices people to perform more online transactions. Cyber criminals love to take advantage of the naïve, stressed out, and busy. According to the national reporting center for fraud and cyber crime, 28,049 shoppers were conned out of their money over the Christmas period last year. This is an increase of almost two-thirds compared to the prior year.
“As the cyber threat landscape evolves, we at Centre are constantly researching and developing our portfolio of comprehensive security solutions to proactively defend organizations from ever-evolving threats.”
Anthony B. Leatherwood, CISSP, CISM, CFE, C|CISO
Chief Information Security Officer for Centre Technologies
When it comes to staying safe amid all of the Black Friday and Cyber Monday deals that will be presented this season, knowledge is power. The following are the top scams that occur during Black Friday and Cyber Monday.
Phishing
 Phishing attacks are fraudulent communications that appear to come from a trustworthy source but can compromise all sorts of data sources. Through phishing, cyber criminals, or "bad actors", send out links to login pages that prompt some sort of authentication from the end-user. During the holiday season, it's common for people to get tricked by these prompts because everyone is looking for a good deal on the products they love.
Phishing attacks are fraudulent communications that appear to come from a trustworthy source but can compromise all sorts of data sources. Through phishing, cyber criminals, or "bad actors", send out links to login pages that prompt some sort of authentication from the end-user. During the holiday season, it's common for people to get tricked by these prompts because everyone is looking for a good deal on the products they love.
Cyber criminals, via well-worded and highly convincing messaging, utilize every tactic they can to get end-users to give valuable information. Thanks to the supply chain issues caused by COVID, cyber attackers are now posing as delivery services. One in 5 (20%) of US citizens have reported this scam this year already.
Smishing
Smishing, like phishing, is when an attacker utilizes well-worded text to trick end-users into clicking a link, sending private information, or downloading malicious programs. The only difference between the two is that smishing happens over mobile.
 If you receive text message updates from your favorite stores or have signed up to secure good deals for Black Friday and Cyber Monday, you'll definitely want to be on the lookout for this one. Information that could be targeted via smishing is information used for identity theft, financial data they can use to sell on darknet markets for online fraud, or online credentials.
If you receive text message updates from your favorite stores or have signed up to secure good deals for Black Friday and Cyber Monday, you'll definitely want to be on the lookout for this one. Information that could be targeted via smishing is information used for identity theft, financial data they can use to sell on darknet markets for online fraud, or online credentials.
A smisher likely utilizes some small amount of your personal information to trick you into thinking the message is legit. This could be information like your name or your address. The end-goal of the text is to get the user to click on the link pointed to an attacker-controlled server. From here, the attacker can either attempt to get information via having the end-user input sensitive information, or, the attacker can silently gather information about the end-user via malware that is used to send sensitive data to an attacker-controlled server.
Scareware
Scareware is a form of malware that utilizes social engineering to shock end-users. It tricks users into believing that the computer has a virus and needs a fake antivirus software. It then prompts users to pay for the "needed" software to remove it. The truth is usually that the virus is fictionaland the software is nonfunctional or malware itself.
While new variations of virus's are released each year, there are signs that usually indicate your computer has one. You're not likely to get a random pop-up encouraging you to purchase a software immediately to ensure that your computer rids itself of the virus.
These messages can appear very convincing at any time of the year, but even more so during the holiday season since people are scanning the internet looking for the best buys and bargains.
Online Payment Skimming
Online skimming or e-skimming attacks steal payment data information by infecting e-commerce websites with malicious codes known as sniffers or JavaScript (JS) sniffers. Once a website is infected, they are hard to detect. Payment information is usually skimmed during a transaction where the end-user has input information from their device without the end-user being aware that their information has been compromised.
Any business that sells products or services online, that does not have the proper security measures in place, can leave themselves vulnerable to hosting this kind of cyber attack on their website. It not only places a damper on business but it offers reputational risks as well.
This kind of scam is hard to spot, as the website would likely look the same to both the consumer and the company itself. It's important to monitor website and financial activity as a business and consumer to ensure no one is being lead astray by skimming.
Financial Malware
Bad actors have designed this breed of malware to steal financial information and embezzle money from the victims accounts using social engineering techniques. These attackers target electronic fund transfers and automated clearing house. While these transfers are protected by financial institutions, the attackers attempt to fool users to hand over their account details.
Usually, bad actors trick end-users into clicking on a certain link or downloading a malicious attachment that comprises of malware but suggests otherwise. This begins the process of infecting the system, which is the first step of implementing financial malware.
After the system is infected, the attackers attempt to lead the victims to enter their personal information through a fraud identification process. Once all of the details are gathered by the malware, the imposters execute fraudulant financial transactions.
Volumetric DDoS Attacks
These kind of attacks can severely impact a websites availability. In a volumetric DDoS attack, a high amount of traffic is sent to the target network in an effort to overwhelm its bandwidth capabilities.
This can cause a website to crash, therefore causing a loss of revenue and brand damage. During the holiday season, this can be incredibly devestating to a companies reputation and its wallet.
Low Volume DDoS Attacks
Low volume DDoS attacks are nicknamed the "trojan horse" DDoS attack. It can go unnoticed by IT security staff and many DDoS protection systems. Because of how undetectable they can be from the onset, these are described as one of the most dangerous cyber attacks.
These attacks, capable of destroying a firewall or intrusion prevention system (IPS), serve as a vessel that hackers can use to target, map, and infiltrate a network to conduct data theft or install some sort of malware or ransomware.
how to avoid being a victim of a black Friday or cyber Monday scam
It may seem that the number of cyber attacks to watch out for are endless and inescapable, but by implementing these basic cyber security best practices, you can avoid provide and enjoy a safe, secure online shopping experience.
Verify the URL
We all receive more email promotions than usual around this time of year, and we must all use a little extra caution before clicking those links to promotions! You’ll also be tracking all the incoming shipping notifications for your time-saving online orders, and though you may have dodged the crowds, try to stay vigilant as you sort through those shipment and delay notifications for your orders. Look for typos in emails or website links, which may indicate a phishing scam or fake links.
While this isn't the only tell that a website is fake, usually authentic websites have what is called a padlock. This is the "HTTPS://" that sits at the front of the URL. If this is implemented, assess the URL for any misspellings and look around the web page to ensure that it is indeed the website you're trying to reach.
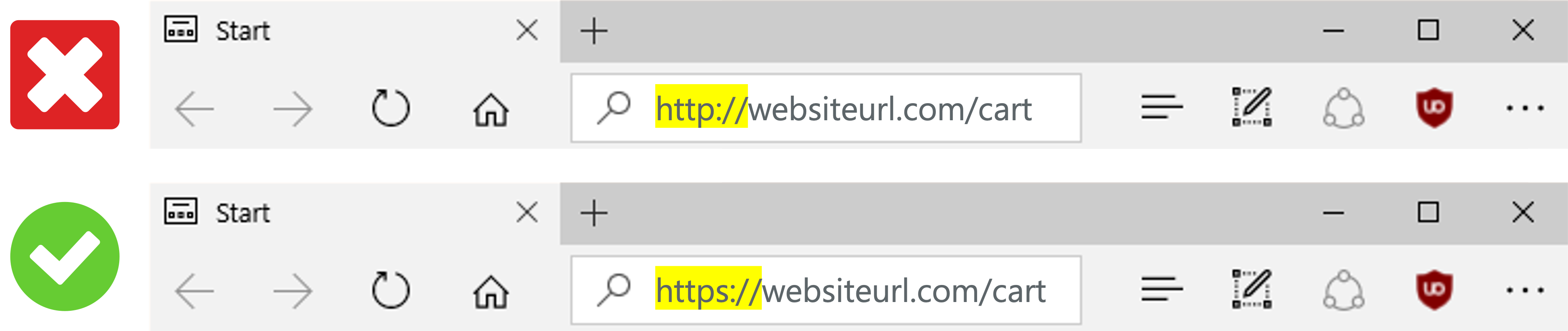
Websites that have security enabled using SSL (Secure Socket Layer) encrypt data during transmission, making it safe to use a credit card on that site. Look for that little lock in the address bar and a URL with “https” instead of “http” at the beginning.
Don't Purchase Things via Mobile without Double Checking the Source
It isn't the safest thing to make online purchases via a mobile device. Oftentimes, you cant see the full URL, and things are expected to look different on a mobile device. Therefore, it's easier to believe that a fake website is real because you're more likely to dismiss the slight differences you see.
Also, there are tons of fake shopping apps out there, so if you want to download a shopping app from your favorite store, best to get it directly from that store’s website to be sure it’s legitimate.
Educate Employees on Cyber Attacks to Expect
95% of cyber security breeches are caused by human error. By increasing employee awareness of cyber threats prevelant during this season, you protect both your employees and your business from cyber attacks that could be especially harmful to your business at this time.
Check Twice Before Giving Out Credit Card Information
Read customer reviews and double check the URL before making an online purchase. Also, note how much personal information is being asked of you before you can submit your purchase. It's highly recommended to use a credit card in case any irregular purchases pop-up that you need to be notified of. Be sure to watch your purchase history as well. It is the only way to tell that you've been a victim of skimming.
Configure Authentication Records like Domain-based Message Authentication Reporting & Conformance (DMARC)
64% of top couriers are at risk of having their domains impersonated by phishers and scammers as a result of not having their Domain-based Message Authentication Reporting & Conformance (DMARC) records set to strict settings. If you want to keep attackers from impersonating your business, you'll need to ensure that your DMARC settings have strict policies set up to guard them.
When in Doubt, Don't Click!
The best form of protection is your intuition sometimes. If something doesn't look right, don't click. It could be a website, a "one time only" bargain, or anything related - odds are if you don't feel right about it, there's probably something that isn't right about it.
"Today's cyber threats are more persistent and pervasive than ever before. While employee awareness can go a long way in regards to covering superficial entry points, only enterprise-grade security protections can actually minimize the impact to systems and reputation in the event of a breach."
Anthony B. Leatherwood, CISSP, CISM, CFE, C|CISO
Chief Information Security Officer for Centre Technologies
Don’t Shop on Hotspots
Just avoid shopping on public Wi-Fi networks, like in airports or coffee shops. While this may seem like the perfect time to knock out that shopping list, open hotspots are extremely dangerous. Hackers have been known to intercept communications between you and the connection point so that instead of talking directly with the hotspot, you end up sending your information to the hacker. In this case, the hacker has access to all the information you send out—emails, phone numbers, credit card information… And once a hacker has that information, you’ve basically given them the keys to your front door. Be sure to keep software up to date on any device you connect to the internet, to help reduce the risk of infection from malware.
Wherever you do find yourself, it’s important to use a VPN (virtual private network) Service which creates a private tunnel from your device to your service. VPN Servers will encrypt your traffic passing through the public Wi-Fi hotspots.
Use Strong and Unique Passwords
Consider making your passwords sentences, like “CountryMusicIsTheBest!2019” and make them unique to every site. Don’t ever use your work email or any variation of your work password on any third-party websites and monitor for exposure!
Consider finishing out the year strong by using a password manager to assist in dealing with the ever-increasing volume of complex and unique passwords and as always, enable multi-factor authentication (MFA) if it’s available from the ecommerce site you are using.
What to do if you've been scammed
Do not be alarmed if you were scammed or someone in your organization was hacked. Taking certain steps can help you fix the damage.
- Should it be an issue involving your organization, contact your IT department immediately. If not, contact your financial institution to request a recall of funds.
- If you believe your credit card number has been compromised, contact your credit card company. You can also report the attack to the Internet Crime Complaint Center. They will report it to federal, state, local, or international law enforcement.
- Should your business have been the target of a network intrusion, data breach, or ransomware attack, contact your nearest FBI field office, or report it at tips.fbi.gov. You can also report it to the State of Texas through texasattorneygeneral.gov.
- Finally, if you suspect that you've been the victim of Identity Theft, visit IdentityTheft.gov.
Stay Safe and Enjoy Black Friday and Cyber Monday Shopping
Since Black Friday and Cyber Monday are events that encourage high volumes of internet activity, it's perilous to engage without being informed of the cyber threats that will be attempting to take advantage of the chaos. With this knowledge, one will be able to navigate all of the bargains presented without being tricked by the frauds.
Are you confident that your business data will be protected in the event of a cyber attack? If your answer wasn't "100% yes!", consider contacting Centre Technologies to create a Backup and Disaster Recovery strategy that strengthens your data protection and reduces revenue loss in the event of a cyber attack.




