The Log4j Vulnerability CVE-2021-44228 Explained
It's been a moment since the CISA announced the Log4j (Log4Shell) security vulnerability. Since then, both IT leaders and business leaders have been scrambling to find out how this security vulnerability may affect their business operations. Publicized in almost every major news outlet, this javascript vulnerability has inspired a rush of attention from businesses towards IT environments and service providers. IT security and manufacturers have started urging customers to enact security updates or prepare for patches. Plenty of these organizations are lost when it comes to understanding Log4j, and how this vulnerability impacts their IT environment—and their business.
Make sure to bookmark this article.
This article is updated regularly to include new developments regarding the Log4j (Log4Shell) vulnerability.
Last Updated December 22, 2021
If you want to get more information on the Log4j vulnerability and what it means for your business, keep reading. You can also tune into our podcast, When Bits Hit the Fan, and listen to the latest episode explaining the vulnerability and if there's any cause for major concern regarding its impact on business.
What is Log4j used for?
Simply put, Log4j is a java-based logging library that gives software developers a way to build a record of activity that can be used for a variety of purposes from troubleshooting and auditing, to tracking data. It is one of the most popular logging libraries used online. And because it is open-source and free, it touches every single part of the internet. The Apache Web Server is a product of the Apache Software Foundation and is one of the most utilized web servers spanning the world, there is no doubt that Apache Web Servers are a high value target for threat actors. With big companies like Amazon, Cisco, IBM, Google, and Apple running the software, millions of devices around the world have the potential to be exposed to the vulnerability.
With the onset of Log4J vulnerability (CVE-2021-44228) and the subsequent mitigation/patching, several new vulnerabilities emerged recently that are also of a high severity associated to the Apache Web Server. We are recommending that any organizations running Apache Web Server to thoroughly test and deploy version 2.4.52 of the Apache Web Server to fix CVE-2021-44790 (CVSS 9.8) and CVE-2021-44224 (CVSS 8.2). Apache Software releases can be found at Apache HTTP Server 2.4 vulnerabilities - The Apache HTTP Server Project.
Already, there have been reports of state-backed Chinese hackers, Iranian hackers, and cryptocurrency miners honing in on it for their own purposes. Hence, why the urgency of conversations about cyber security is intensifying. In fact, a recent FBI bulletin states that organizations can expect this vulnerability and other related issues to extend well into April of 2022.
When was the Log4j Vulnerability discovered?
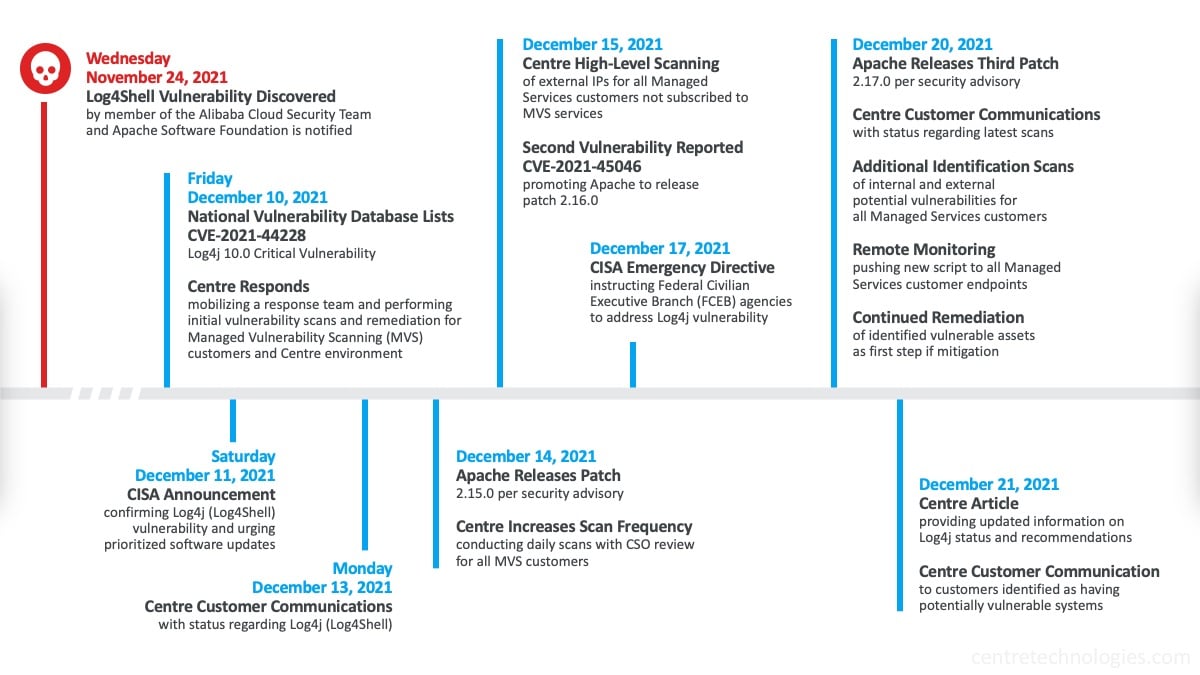
On November 24th, 2021, Chen Zhaojun - a member of the Alibaba Cloud Security Team - discovered the Log4j vulnerability (labeled Log4Shell and officially named CVE-2021-44228) and alerted the Apache Software Foundation. The Log4j vulnerability was added to the National Vulnerability Database (NVD) list as a 10.0 Critical Vulnerability on December 10th. The next day, the Cybersecurity and Infrastructure Security Agency (CISA) then released a statement encouraging organizations to protect themselves against the vulnerability. On December 17th, the CISA issued an emergency directive requiring federal civilian departments and agencies to mitigate apache Log4j vulnerabilities.
Centre increased scanning frequency for Managed Vulnerability Scanning (MVS) customers and conducted manual reviews of external IP addresses for those not subscribed to MVS services starting December 14th.
What does the Log4j Vulnerability mean for businesses?
One would think that only the most sophisticated hackers can exploit this vulnerability but that is far from the truth. In order to exploit this vulnerability, an attacker does not need advanced experience in programming or some sort of engineering background. With a single line of code, someone exploiting Log4j could gain remote access to any device. Bad actors have also begun using Log4j to deploy ransomware with a new ransomware variant named Khonsari discovered by Bitdefender and later confirmed by Microsoft. We also know that Conti ransomware operators have begun targeting a Log4Shell vulnerability.
Organizations attempting to patch systems for the Log4j vulnerability are having to consider potential VMware issues, Apache issues, Google "Log4j bug" notices, and related challenges. Businesses may need to assess their vendors and even the vendors of their vendors to assess whether they've been impacted by Log4j.
What can businesses do now?
It's critical that in the midst of the sense of urgency to defend against this vulnerability, businesses remain calm yet steadfast about implementing a proactive defense plan. Partnering with a Managed Services Provider (MSP) that has extensive cybersecurity expertise and partnerships is the first step a business can take in defending against Log4j. For example, Centre mobilized a Tactical Response Team to focus on assessing the environments of Managed Services customers to identify potential vulnerabilities related to Log4Shell. Centre's team of security experts then worked with customers to develop mitigation and remediation plans.
Businesses interviewing MSP's or waiting on scope estimates can take advantage of the following free tools in the meantime. All of which have been recently released by various cybersecurity services:
- Amazon Web Inspector (https://aws.amazon.com/inspector)
Automated security assessment service deployed on AWS that works to improve the security and compliance of applications. - Arctic Wolf Log4Shell Deep Scan (https://github.com/rtkwlf/wolf-tools/tree/main/log4shell)
A script that detects Java application packages subject to Log4j vulnerability. - Qualys Web Application Scanner (https://www.qualys.com/forms/web-application-scanning-log4j)
A cloud-based service that provides automated crawling and testing of web applications to identify vulnerabilities.
Email is one of the most overlooked vectors to exploit. Businesses need to be cautious of suspicious emails and report them immediately. Here at Centre, we are working through cybersecurity partners in the Texas region. As of December 22, several active Threat Actor Groups have been identified as leveraging email phishing and Log4j/Log4Shell to access privileged systems by repurposing exploit code.
While there are security controls to defend against most phishing attempts, there are always threat actors attempting to circumvent those controls. Best advise: Organizations need to stay vigilant and watchful.
How to avoid similar vulnerabilities in the future?
The unfortunate reality about threats like Log4j is that they are a dime a dozen. You can't predict when they will be exposed and when bad actors will attempt to take advantage of them. The best course of action to take in order to prevent vulnerabilities like Log4j from impacting your business is to utilize Managed Vulnerability Scanning (MVS).
MVS is a service that provides a regular assessment of an organization's public-facing infrastructure to regularly identify exploitable vulnerabilities and reduce the potential window of exploitation for attackers. Many businesses install antivirus software and call it a day. Server defenses need to be fortified with security protections that don't rely on traditional antivirus signatures (also known as Indicator of Compromise or IOC). Incorporating threat hunting services like Managed Detection and Response (MDR) services provides a more adequate defense from vulnerabilities like Log4j.
"Centre works with several agencies and strategic partners to stay ahead of both non-disclosed and publicly disclosed vulnerabilities daily. Each risk is assessed with a vulnerability score factoring the impact severity to Confidentiality, Integrity, and Availability (CIA Triad). We work across industry partners to deploy countermeasures that safeguard customer environments."
Anthony Leatherwood CFE, M.Jur., C|CISO
Chief Information Security Officer at Centre Technologies
The Center for Internet Security (CIS) posted a security benchmark of requirements that includes Continuous Vulnerability Management. Centre Technologies' Managed Vulnerability Scanning meets CIS criteria across all requirements. Centre's team of cybersecurity experts take a proactive approach to eliminating vulnerabilities like Log4j through frequent comprehensive scanning and remediation. By enacting rigorous vulnerability prioritization and strategic security consulting with tactical remediation, Centre customers are able to stay ahead of evolving threats. Take the first step towards protecting your business data and contact Centre to learn more about Managed Vulnerability Scanning today.
Additional References
-
ConnectWise has provisioned a new capability to help partners automatically detect any potential Log4j vulnerabilities.
-
Tenable has released scan templates that are pre-configured for this vulnerability.
-
CrowdStrike released a blog showing it can detect Indicators of Attack (IOAs) from this vulnerability.
-
SentinelOne will alert on Indicators of Attack (IOAs), but no formal out of band functionality or tools have been listed.
-
Microsoft Defender for Endpoint has updated their capabilities in response to the threat.
-
Qualys has made a Web Application Scanning Solution available FREE for 30days.
-
CloudFlare added rules for clients using the CloudFlare WAF to help mitigate any exploit attempts.




