The Follina Zero-Day Vulnerability CVE-2022-30190 Explained
This week Microsoft announced a zero-day exploit named "Follina" that leverages a bug in the Microsoft Support Diagnostic Tool (MSDT). Since Microsoft's announcement, both IT leaders and business leaders are looking to find out how this vulnerability may put their business operations and Microsoft Office data at risk. Now publicized on many mainstream news outlets, this latest Microsoft vulnerability has inspired a rush of attention from businesses to seek advice from certified Microsoft Cloud Solution Providers (CSP) that specialize in cybersecurity pending a Microsoft patch for the Follina exploit.
Make sure to bookmark this article.
This article is updated regularly to include new developments regarding the Follina (CVE-2022-30190) vulnerability.
Last Updated June 3, 2022
If you want to get more information on the Follina vulnerability and what it means for your business, keep reading.
What is the Microsoft "Follina" Zero-Day Vulnerability?
Simply put, the Microsoft zero-day exploit "Follina", assigned CVE-2022-30190, allows hackers to execute PowerShell commands across Microsoft Office application by leveraging a bug in the Microsoft Support Diagnostic Tool (MSDT) and executing remote code.
This threat is considered severe and can lead to a complete compromise of data and systems due to granting hackers the ability to elevate privileges and gain complete access to the affected environment. Once a business is breached using this Follina exploit, hackers are able to install malicious programs, view, change, create endless user accounts, and even delete data.
Already, there have been reports of state-backed hackers using this Microsoft vulnerability in an increasing number of attacks. Microsoft has not released a patch for this exploit to date.
When was the Microsoft "Follina" Exploit discovered?
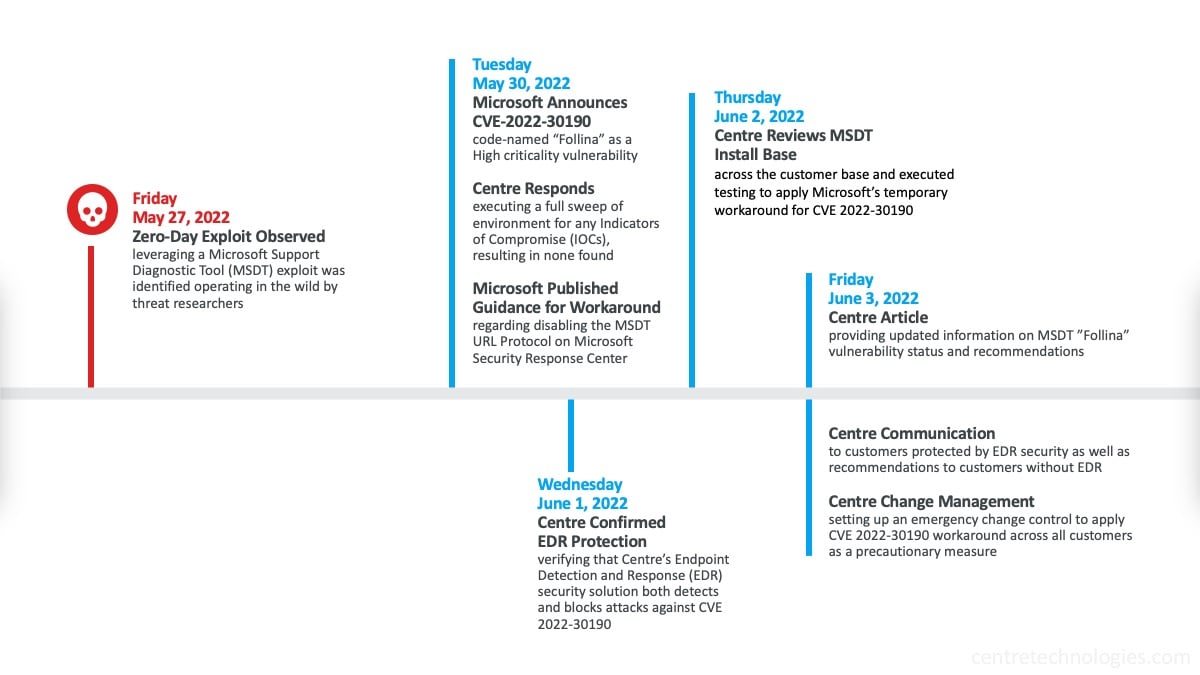
Originally observed in an attack involving a malicious document file on May 27th, a former Microsoft Senior Threat Intelligence Analyst and now researcher, Kevin Beaumont, named the exploit "Follina". On May 30th, Microsoft formally announced CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability in a post on the Microsoft Security Response Center website. Since its announcement, various Managed Detection and Response (MDR) providers released statements that they were keeping a close eye this developing zero-click threat that uses a Technique, Tactic, and Procedure (TTP) of remote code execution through Microsoft Support Diagnostics Tool (MSDT) and Microsoft Office applications like Microsoft Word. Cybersecurity professionals expect exploitation attempts to evolve to email-based delivery.
Since Endpoint Detection and Response (EDR) security services are included as part of Centre's Secure Managed Services, customers enrolled are protected from this exploit.
What does the MSDT Exploit mean for businesses?
Businesses of all sizes use Microsoft Office as part of their daily operations. That's over eight-hundred thousand and nearly 83% of enterprise businesses. With this unpatched exploit, applications such as Microsoft Word now put employees and businesses at risk for a wide-spread breach.
While many businesses may have some sort of cybersecurity protection like anti-virus or have enacted best practice for access policies and admin-level privileges, file-less threats are often hiding in plain sight. While Endpoint Detection and Response (EDR) security services is considered the gold standard for protecting all endpoints from such zero-day exploits, tools that provide "application whitelisting" and "ringfencing" protections can also help. Solutions like ThreatLocker pivot application controls, data storage controls, and elevation controls from a "trust all, except" rule to "trust none, except these specific applications, ran by this specific person, on this specific device, on this specific IP address only" rule.
What can businesses do now?
While Microsoft hasn't released a patch for the MSDT exploit "Follina", Microsoft has published a workaround to disable the MSDT URL Protocol (see Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability – Microsoft Security Response Center). As a Managed Services Provider (MSP) that's also a Managed Security Services Provider (MSSP), Centre Technologies is following Microsoft’s guidance and actively assessing the feasibility of disabling MSDT URL Protocol for customers not already enrolled in Secure Managed Services that includes Endpoint Detection and Response (EDR) security.
How to avoid exploits like "Follina" in the future
The unfortunate reality about zero-day exploits like the Microsoft "Follina" vulnerability is that they are discovered almost weekly. You can't predict when they will be exposed and when bad actors will attempt to take advantage of them. The best course of action to take in order to prevent from them impacting your business is to utilize ensure you have proactive security scanning, endpoint security protections for devices and a clean and current backup of devices, cloud environments, and files.
"Centre works with several agencies and strategic partners to stay ahead of both non-disclosed and publicly disclosed vulnerabilities daily. Each risk is assessed with a vulnerability score factoring the impact severity to Confidentiality, Integrity, and Availability (CIA Triad). We work across industry partners to deploy countermeasures that safeguard customer environments."
Anthony Leatherwood CFE, M.Jur., C|CISO
Chief Information Security Officer at Centre Technologies
Managed Vulnerability Scanning
Managed Vulnerability Scanning (MVS) is a service that provides a regular assessment of an organization's public-facing infrastructure to regularly identify exploitable vulnerabilities and reduce the potential window of exploitation for attackers. Many businesses install anti-virus software and call it secure. Fortified cybersecurity is not relying solely on traditional anti-virus signatures, also known as Indicator of Compromise (IOC).
Managed Detection and Response
Incorporating threat hunting services like Managed Detection and Response (MDR) services provides a more adequate defense from vulnerabilities like "Follina". With Endpoint Detection and Response (EDR) agents, attempts to hack or exploit files or systems are automatically contained.
Backup and Disaster Recovery as a Service
Traditional backup methods are not enough to ensure a successful recovery from a breach. Investing in a full, not a piecemeal solution, that includes Disaster Recovery (DR) is essential. Organizations big and small partner with Centre for Backup and Disaster Recovery as a Service (BDRaaS) that includes best practice security configurations and supports unlimited retention of cloud data for SaaS applications, like Microsoft 365 and Microsoft Office, as well as for cloud services like Azure Active Directory.
Is your business protected from exploits?
"Follina" is just one of the many exploits that are discovered every year. Because of the volume of exploits, many businesses tend to become complacent, thinking these exploits have little to no impact. While for some that may be true, for many others these exploits are the cause of thousands of dollars in damages. If you're not sure how protected your business is against these exploits, contact Centre Technologies today.
Additional References
-
Microsoft has published Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability.




