Microsoft 365 Defender vs. Other Security Services
Businesses are increasingly challenged trying to find out if having Microsoft Defender is enough security to keep their employees, data and bottom line protected for evolving security threats. In 2021, a reported 250,000 Microsoft servers were targeted by hackers, some of these servers belonging to 30,000 organizations in the United States. 67% of IT leaders have reported an increase in data breaches due to remote work. With that number expected to grow in 2022, Microsoft is updating its security products to help better protect endpoints. That said, even with these planned updates to Microsoft Defender blind spots remain that require other security services for full protection.
What is Microsoft Defender?
Microsoft Defender is an anti-malware component of Microsoft Windows. Initially, it was a downloadable free anti-spyware program for Windows XP that was called "Windows Defender", released in 2006. When Windows Vista was released in 2007, Windows Defender was already preloaded into the operating system, providing an indigenous anti-spyware tool. Users would still need to download a separate anti-virus program, however, to provide complete protection. Windows Defender was also built into Windows 7 when released in 2009, Windows 8 in 2012, and versions down the line. Before Windows 8, Windows Defender only protected users against Spyware.
With the release of Windows 8, protection against viruses was added, resembling Microsoft Security Essentials (MSE), using the same anti-malware engine and virus definitions. In Windows 10, while usually available in the settings app, Microsoft Defender settings moved to the Windows Defender Security Center. Microsoft also released a feature in the anniversary release of Windows 10 where users would receive a pop-up notification after a scan reflecting the findings even if no viruses were found.
While Microsoft Defender is highly effective software that scans email, internet browser, cloud, and applications for cyber threats- it lacks endpoint protection and response. It also lacks automated investigation and remediation of threats. Therefore, Microsoft Defender is software that needs to be paired with other antivirus software in order to function successfully.
Here at Centre, we offer a robust program for businesses that run Microsoft 365 with us. It is secure by default because we automatically include the protections that programs pre-installed with Microsoft, like Microsoft Defender, don't have.
Microsoft Defender for Endpoint
Previously known as Microsoft Defender Advanced Threat Protection, Microsoft Defender for Endpoint is an endpoint security solution that offers vulnerability management, endpoint protection, detection, response, and automatic investigation and remediation. It uses a combination of endpoint behavioral sensors, cloud security analytics, as well as behavioral and cloud-powered threat intelligence to provide what Microsoft calls "next-generation protection".
In order to have access to Microsoft Defender for Endpoint, users need the Microsoft Defender for Endpoint Plan 1 (P1) or Plan 2 (P2). Both P1 and P2 is available on its own as a user subscription license for commercial and education customers. It is also what is included with certain Enterprise and School licenses.
For detailed information on the licenses that contain Microsoft Defender for Endpoint, you can get in touch with Centre's Microsoft cloud and security consultants.
Microsoft Defender P1 includes next generation anti-malware, attack surface reduction rules, device control, endpoint firewall, network protection, and more. Meanwhile, Microsoft Defender P2 includes everything encompassed in P1 and additional capabilities such as endpoint detection and response, automated investigation and remediation, threat and vulnerability management, threat intelligence, sandbox, and Microsoft threat experts.
Microsoft Defender for Office 365
Developed to help protect organizations against sophisticated attacks like phishing and zero-day malware, Microsoft Defender for Office 365 correlates signals from a broad range of data to help identify, prioritize, and provide recommendations on how to address potential threats.
Previously known as Office 365 Advanced Threat Protection, Microsoft Defender for office 365 is available in two different plans. Defender for Office 365 Plan 1 comes with configuration, protection, and detection capabilities like:
- Safe Attachments for SharePoint, OneDrive, and Microsoft Teams
- Safe Links
- Anti-phishing protection
- Real-time detections
- Safe Attachments
Microsoft Defender for Office 365 Plan 2 includes all of the above Plan 1 capabilities, PLUS:
- Threat trackers
- Threat explorer
- Automated investigation and response
- Attack simulation training
Microsoft Defender for Office 365 is largely used to prevent broad, volume-based, known attacks but is only available exclusively for certain licenses. For more information on what these licenses are, contact one of our IT Consultants here.
Microsoft Defender for Identity
This cloud-based security solution leverages on-premises Active Directory signals in order to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Previously known as Office 365 Advanced Threat Protection, Defender for Identity gives SecOp analysts and security professionals the ability to detect advanced attacks in hybrid environments. With Microsoft Defender for Identity, users will have the ability to:
- Monitor users, entity behavior, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activity and advanced attacks
- Report clear incident information on a simple timeline for fast triage
By leveraging on-premises Active Directory signals, Microsoft Defender Identity can offer businesses a sound threat protection and prevention system. Like the former applications stated, Microsoft Defender Identity is only available with certain licenses.
Microsoft Defender for Cloud Apps
One of the benefits of moving to the cloud is increased flexibility. That said, this increased flexibility requires an increased set of security measures. Microsoft Defender for Cloud Apps provides a suite of security features to ensure that there is a balance of supporting access while protecting critical data.
Microsoft Defender for Cloud Apps is a Cloud Access Security Broker (CASB) that operates on multiple clouds. Previously known as Microsoft Cloud App Security, this solution is built to provide comprehensive security and compliance in order to enable users in any organization, located both locally and remote, to adopt business applications without compromising efficiency.
This solution helps users to gain visibility of deployed cloud apps, discover shadow IT, and protect sensitive information. It also contains protection against cyber threats, assesses compliance, and manages security posture across clouds whilst supporting cloud-native applications.
Because Microsoft Defender for Cloud Apps is a security tool, it doesn't require Office 365 productivity suite licenses. However, there are certain prerequisites that need to be met in order to set it up. While an organization or business could attempt to set this up themselves, it's best to utilize an MSP to speed up the setup process with accuracy.
Microsoft Defender XDR
Microsoft 365 Defender is an extended detection and response (XDR) response solution. XDR solutions provide protection from a wide range of threats that could come in contact with your endpoints, network, users, and cloud workloads. This is done by providing continuous and automated monitoring, analysis, detection, and remediation.
Microsoft 365 Defender does this specifically for your Microsoft 365 environment, and covers applications, email, and identities. It automatically collects, correlates, and analyzes signal, threat, and alert data. Microsoft 365 Defender utilizes AI and automation to stop attacks involuntarily and remediate affected assets to a safe state. It consists of:
- Microsoft Defender for Identity
- Exchange Online Protection
- Microsoft Defender for Office 365
- Microsoft Defender for Endpoint
- Microsoft Defender for Cloud Apps
- Azure AD Identity Protection
Because the threat landscape is increasing in sophistication and complication, XDR presents a new, advanced approach in order to deliver security that is built to withstand the ever-evolving threats of today. To learn more about this solution and how to activate it for your business, contact our IT Consultants here.
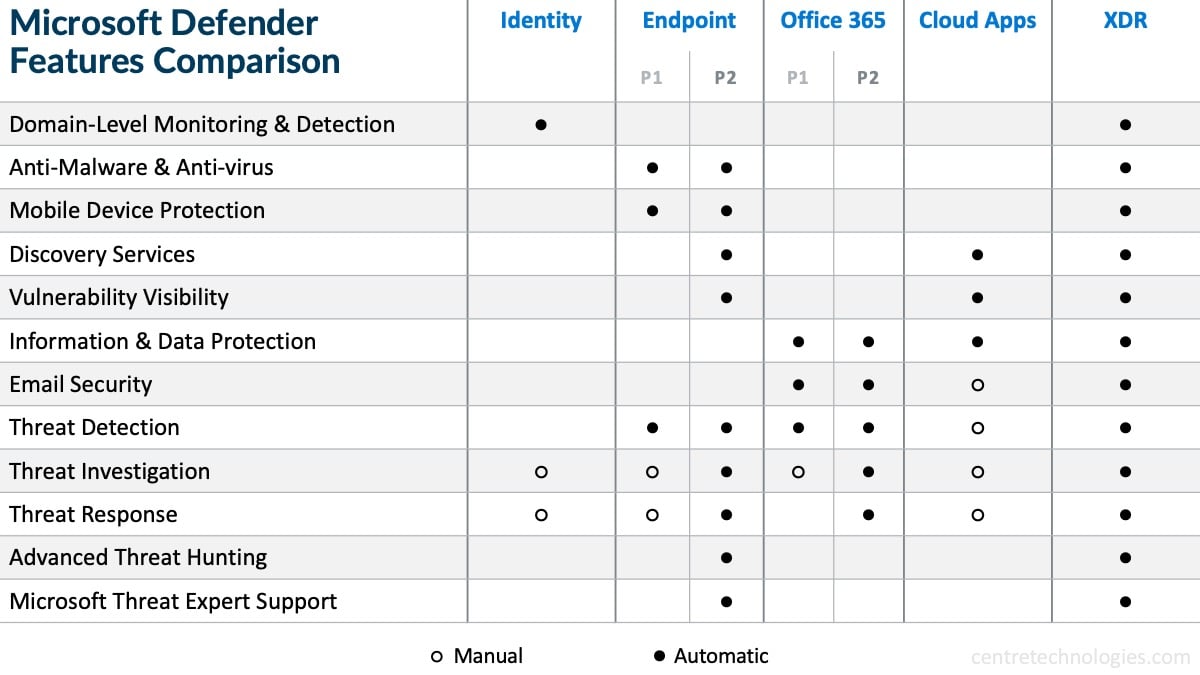
Differences Between Microsoft Defender Services
Each Microsoft Defender Service is built to provide businesses with security measures and controls that are best suited for them. It's the reason why not all protections and preventative measures are included with every license. Taking a look at the table below, you can see that only XDR offers every capability.
To determine which license your business would benefit from the most, our IT Consultants, who are well-versed in Microsoft Defender solutions, can help you figure out the best solution for your business or organization.
What's New for Microsoft Defender?
Threat and Vulnerability Management
As remote work is popularized and hybrid work environments persist, threats continue to transform and advance. Microsoft Defender has included threat and vulnerability management made to help recognize threats, such as the recent Log4j vulnerability, hiding in applications and components.
By identifying, assessing, and remediating endpoint weaknesses, the threat and vulnerability management enhancement to Microsoft Defender reduces risk for businesses and organizations.
IoT (Internet of Things) Device Discovery and Integration
The Internet of Things (IoT) Device Discovery and Integration has the ability to help you find unmanaged IoT devices connected to corporate network(s). It also gives a single, unified view of IoT inventory alongside the rest of an organization's IT devices (workstations, servers, and mobile).
By enhancing device discovery with the agent-less monitoring capabilities provided by Microsoft Defender for IoT, businesses can increase visibility to help locate, identify, and secure the IoT devices in the network.
Is Microsoft Defender good enough?
Here's How to Cover blind Spots
Many people are surprised when the same IT environment that they've invested time and money to secure ends up attacked. The truth is, there are blind spots both known and unknown that can make it fairly easy for hackers to make an entrance and wreak havoc. An object is only as strong as its weakest point, and the same goes for an IT environment.
Unpatched systems, phishing, ransomware, encryption issues, and more are just a few of the most common blind spots in a supposedly "secure" IT environment. It's these very blindspots that cause businesses millions of dollars and contribute to the foreseen estimate that cyber crime will cost the world $10.5 trillion by 2025.
In order to house a fully secure environment, ready to face the threats of today and tomorrow- businesses need to utilize a robust program. Unfortunately, Microsoft Defender XDR, with as much as it offers, isn't enough by itself. Using an MSP like Centre will help to cover the blind spots that are notorious for being open doors for cyber threats.
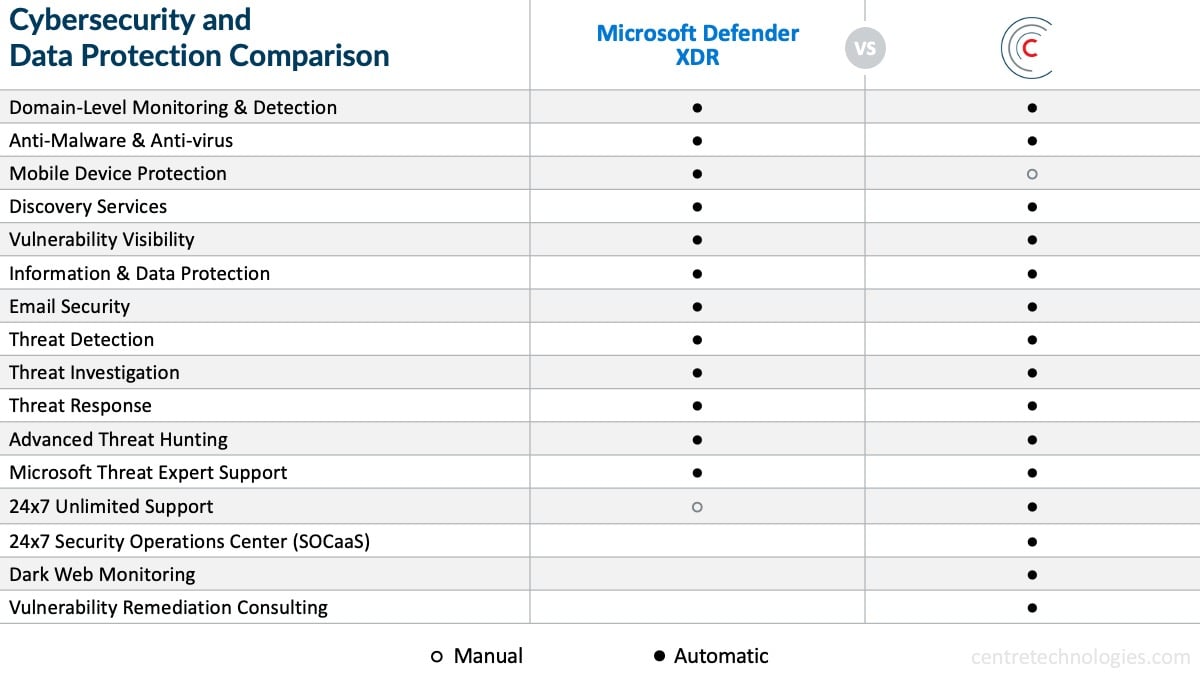
Better Visibility of Blind Spots with Managed Vulnerability Scanning
It is impossible to predict when they will be exposed and when bad actors will choose to take advantage of them. Managed Vulnerability Scanning (MVS) is the best method to prevent vulnerabilities such as Log4j from negatively impacting your business.
Vulnerability management service (MVS) is a service that evaluates the public-facing infrastructure of a business regularly to identify exploitable vulnerabilities and reduce the window of exploitation for attackers.
Enhanced Protection with Managed Endpoint Detection and Response
While Microsoft Defender offers XDR, but this does not cover a business's entire IT environment. It is only half of an entire solution. Hence, why it can still leave a business vulnerable to threats.
When utilizing EDR with Security Operations Center-as-a-Service (SOCaaS) services with Centre Technologies, businesses get full protection via threat monitoring, data analyzing, threat pattern identification, and immediate response to threats. Not only do businesses get to experience effective detection and automatic containment of endpoints, but in doing so, they can prevent ransomware attempts such as the highly publicized Colonial Pipeline cyber attack.
Quick Recovery with Cloud Backups and Disaster Recovery Services
Regardless of the event, disasters can happen at any time. With the help of cloud backup and disaster recovery services, businesses can create disaster recovery systems that are dependable and improve business strategy.
From workstations and devices to cloud apps and on-premise servers, a reliable cloud backup and disaster recovery program makes all the difference in how efficiently an organization is able to operate.
As a result of the new features and enhancements in Microsoft Defender, businesses are able to be more secure, productive, and efficient. Get in touch with Centre Technologies today to book a guided tour of Microsoft 365 with security enhancements.
Be a thought leader and share:
About the Author
Organizations entrust Centre with protecting their technology ecosystem and strengthening their security posture. Centre’s cybersecurity and compliance solutions delivers layered IT security to protect businesses’ employees, customers, and content from known and unknown threats. Through employee awareness training, detailed security assessments, and 24x7 threat containment, Centre is a trusted partner for businesses seeking comprehensive network and data protection. Learn more about Cybersecurity and Compliance »


