Executives Prepare for a Cyber Storm
2020 has blown a storm of activity affecting businesses of all sizes, and we are only half way through the year. Businesses all over the world have experienced a dramatic shift in what, when, and how they work. Along with this shift, extreme reliance on IT infrastructure and systems has pushed employees, IT support teams and technology providers out of their comfort zones and into the harsh reality of mass adoption of new work methods in a short time frame.
Flash back to the end of 2019, majority of businesses were finalizing budgets and plotting their course into next year's journey. Confident and armed with the tools needed to thrive, 2020 arrived and you left the safe shore and ventured out to sea. Less than a quarter of the way into your journey, you are violently thrown off course by one of the worst storms in history that not even the greatest meteorologists could have predicted. Now, you are completely off course and your navigation tools have failed you. What now?
Navigating the new landscape
As we look to navigating the new landscape, cybersecurity is a familiar obstacle and has been increasingly high on the priority list for businesses and organizations for the last several years. Since COVID-19, the familiarity and need of cybersecurity has changed for business owners, operators, and employees.
Even though experts relied heavily on security reports to plan for 2020, what they had in mind in Q4 of 2019 has shifted due to the sudden change and need for businesses to adapt to a remote workforce.
Cybersecurity now dominates the priorities of every organization as each adapts to a post-COVID 19 world. Remote workers identities’ and devices are the new security perimeter.
– Louis Columbus, Senior Contributor – Forbes.com
As we look through the updated Cybersecurity Forecasts, there are some key threats that may be even more relevant in our “New Normal.”
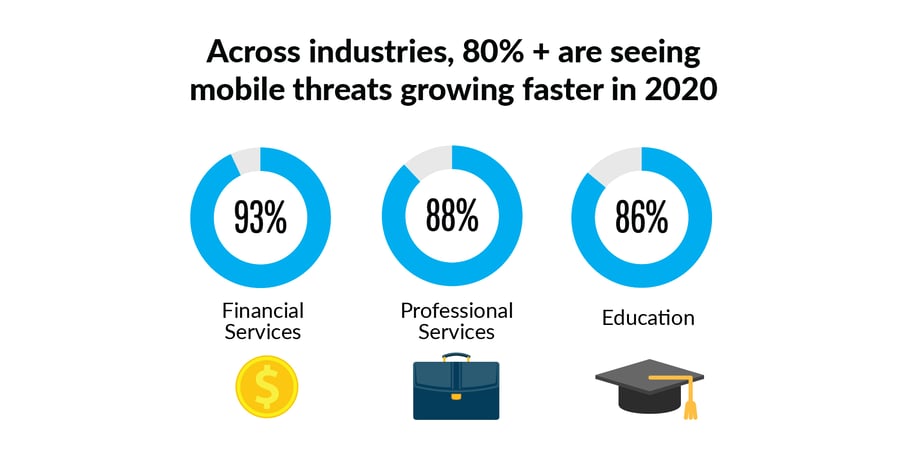
Threat: Mobile Security
With the increased amount of dependability on our remote devices, it's no surprise that 87% of enterprises are seeing mobile threats growing the fastest this year, outpacing other threat types, based on Verizon’s Mobile Security Index 2019. This means that your employees' mobile devices and unsecured networks can introduce significant risks to your business and data.
Cyber criminals continually focus on Microsoft Office 365 making it one of the most targeted brands in the world due to its popularity and adoption across the globe. The email and productivity suite are leveraged by over 1 million companies worldwide. With so many businesses relying on this platform for critical business applications and communications, breaching a business account can prove to be very lucrative for cyber attackers and criminals.
With a single set of compromised credentials, hackers can launch spear phishing attacks from within the organization. This can lead to theft of valuable data, financial losses due to illegitimate wire transfers, ransomware and more.
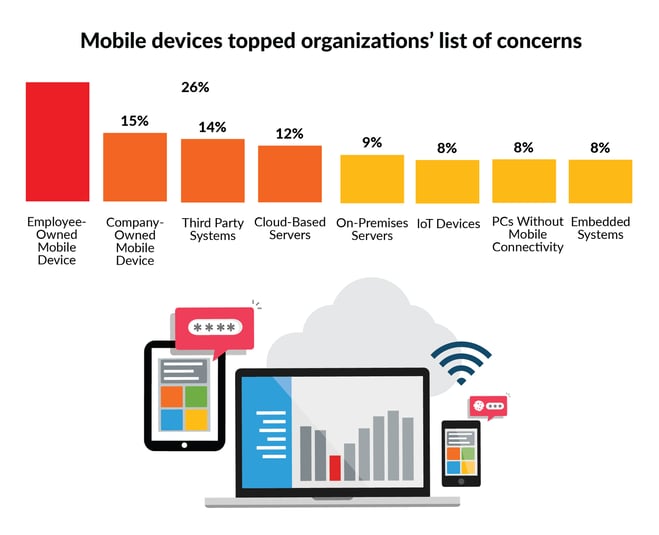
Threat: Single Strategy Approach
Businesses primarily focus their risk management strategies on technological defenses. Historically, this means investments in hardware and licensing. Meanwhile, investment in tools and processes to improve employee access, rights management or company training for Business Readiness and Disaster Recovery tend to be neglected.
According to a Microsoft Global Cyber Risk Perception Survey, results show:



The average cyber-attack costs small businesses $200,000. That cost grows exponentially based on the size of the business, industry, etc. According to a report from Google, "these nefarious actors are proving to be very successful. Google found there were 149,195 active phishing websites in January. That number rose by 50% in February to 293,235 websites. By March, there were 522,495 — a 350% increase since the beginning of the year.”
Threat: Collaboration Platforms
To aide businesses during the Coronavirus pandemic, many major collaboration tool providers offered free or steeply discounted products. One such tool, Microsoft TEAMS, showed an increase of over 70% in active daily users. Most recent reports show over 75 million active users leveraging the Microsoft TEAMS platform for collaboration, video, and phone calls.
A new report reveals how security researchers have observed thousands of cloned Microsoft Team login pages being used in an attempt to harvest account passwords.
– Davey Winder, Senior Contributor – Forbes.com
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn how a hasty deployment can lead to oversights in security configurations and undermine a sound O365-specific security strategy.
Zoom, the popular video conferencing solution leveraged by businesses, schools, medical professionals, and even social gatherings has seen a tremendous adoption increase over the past few months. For all its ease of use and flexibility, Zoom makes it easy for malicious attackers to compromise open meetings. Creating a huge "attack surface", the platform is an open invitation to hackers. Hacker groups have already registered Zoom-related phony domains and are developing Zoom-themed malware. The upside is that flaws are found and fixed relatively quickly, especially when leveraging the web browser version.
Talos, an information-security research firm owned by Cisco, revealed June 3 that it had found two serious flaws in Zoom client applications.
The first flaw would have let an attacker use a specially created animated GIF placed in a Zoom meeting chat to hack Zoom client software on other people's machines to force the installation of malware, or, as Talos put it, "achieve arbitrary code execution." The second flaw also involves the chat function in Zoom meeting client software, with similarly serious potential consequences. The problem was that Zoom did not validate the contents of shared compressed files such as .zip files. Both flaws have since been resolved.
Private Equity and Venture Capital Firms
Cybersecurity has become a critical component of due diligence for Private Equity (PE) and Venture Capital (VC) firms due to the risks associated. In the event that a company under the PE or VC umbrella is attacked, most companies do not know who to call. They certainly do not think to call their PE or VC firm.
You’re telling attackers you’re going to inject a large amount of capital into a company that presumably has valuable intellectual property...It’s like giving them a road map to the pot of gold.
– Mike O'Malley, Vice President – Radware
PE / VC firms are beginning to construct “consortium” partnerships for this very reason. In IT, they analyze their portfolio company’s IT landscape, make recommendations, analyze in-house IT and current 3rd party partners, and determine competence. If found incompetent, the Portfolio company will recommend a pre-vetted IT partner like Centre Technologies, who has extensive amount of experience with over 60% of their current customers being Private Equity backed.
In conclusion, a multi-layered security strategy and approach is the best way to avoid and minimize risks. Staying ahead of industry news and the ever-changing cybersecurity threat landscape allows you to adjust priorities and evolve your approach as quickly as possible. Partnering with cybersecurity and information security experts affords your team the luxury of focusing solely on the business.
Be a thought leader and share:



