Why Immutable Backups are Key for Data Protection and Cybersecurity
Incorporating immutable backups as part of your data protection strategy can make the difference between successful disaster recovery and paying thousands in ransomware—only to find out that your backups have been trashed.
But your business has done all the right things, right...right?
Networked and secured on-premise servers? Check.
Migrated common applications and software to cloud-based services? Check.
Installed anti-virus and threat detection services on all storage and compute endpoints and cloud environments? Check.
Implemented backup solutions for both on-prem, cloud and Software-as-a-Service (SaaS)? Check.
Yet, even with all of the right things in place, the potential threat of falling victim to ransomware remains.
Why Backups are Important
Backups are fundamental when it comes to protecting your data. Backups are part of multiple parts of the CIA triad. If you are unfamiliar with the CIA triad, it's a set of principles that govern cybersecurity. The "C" in CIA stands for confidentiality—making sure that your data is only disclosed to the people that are authorized to know about it. The "I" is for integrity—making sure that your data is reliable and unchangeable unless there is authorization to do so. The "A" in the CIA triad stands for availability—ensuring that your resources and data can be accessed when they are needed.
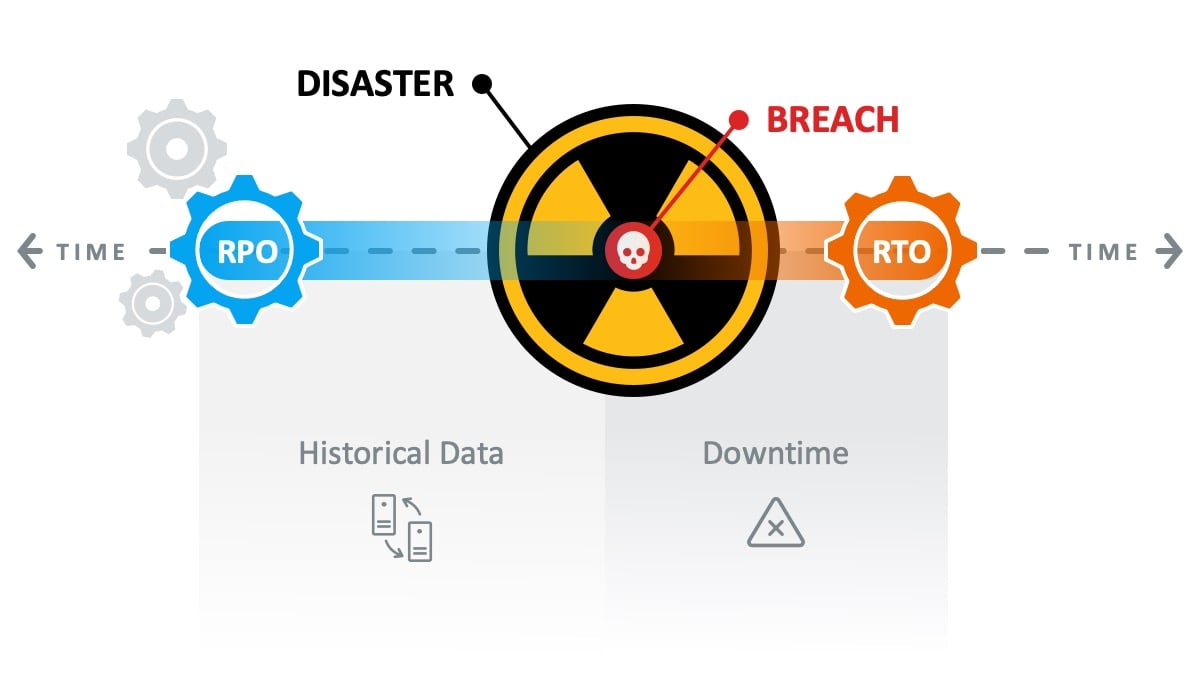
Once it has been determined how a breach occurred and a disaster recovery plan is in place, backups are often used to restore data that was corrupted on the affected servers. Recovering from backup is critical in most cases. Backups provide a Recovery Point Objective (RPO) of historical data before the attack happened. This is commonly days or weeks of backed-up data. While backups are not only a tool for IT professionals to use, they are a target for attackers to exploit when looking for important data in your environment. Attackers will often use tools for data reconnaissance within your environment, learning where your most valuable data is stored as well as backed up. To up the ante, bad actors will then encrypt and thrash that data (including associated backups) to negatively impact your Recovery Time Objective (RTO) to extend your downtime to the point that you'll pay almost anything to stop the bleeding.
Prime targets for hackers range from credit card information to health information, Social Security information, and trade secrets. Once hackers acquire your sensitive data, they either sell or hold your data for ransom. After acquiring their primary targets, attackers often will look for associated backup servers and any attached storage within your environment.
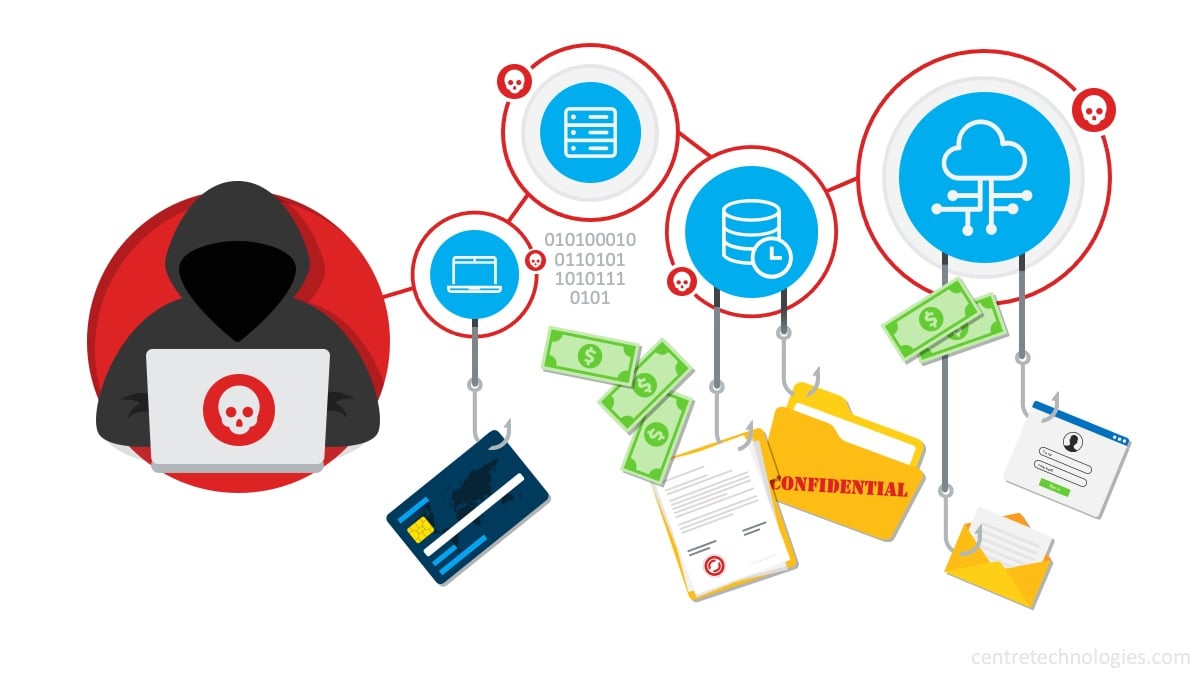
Attackers secure their hold on your data by corrupting or destroying any snapshots or data that is stored on those devices. For the hacker, this ensures that you're unable to restore data, and thus forced to pay their ransom to regain access to your data—or what's left of your data.
Protecting Backups from Ransomware
There are various steps you can take to protect your organization's backups that are considered best practices for all IT environments. All of these can be found in most of the cyber security insurance requirements today.
Schedule Backup Recoverability Testing
First and foremost is to ensure that your backups are usable. This approach does not stop at a successful backup—it's only the start. To ensure that your backups will be ready when you need them, they need to be tested on a regularly scheduled basis.
Adopt 3-2-1 Rule for Backups
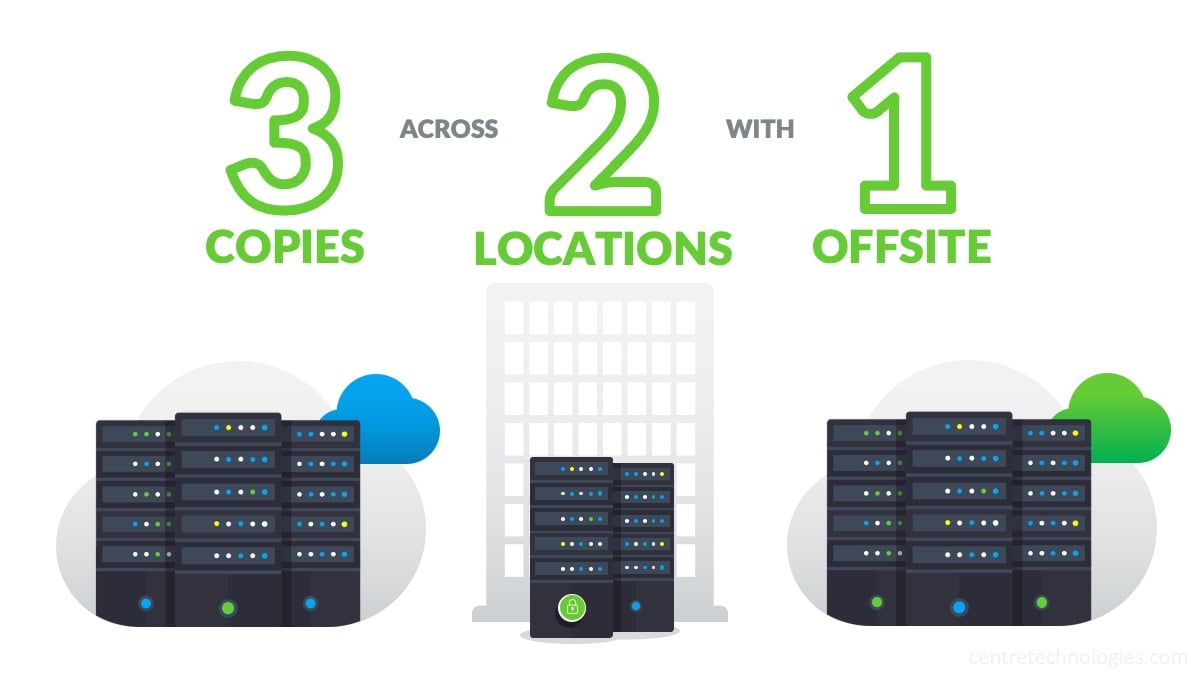
Next, ensure that you have the appropriate number of copies of your data by following the 3-2-1 rule for backups: Three (3) copies of your data, stored in two (2) separate locations or types of media, with one (1) of those copies being stored offsite.
Separate Administrative Credentials
The next best practice step is to use administrative credentials to store your backups separate from any other administrative account in your environment. Utilizing separate credentials helps to ensure that if an administrative account is utilized that it will not have access to the backup environment.
Segment Backup Servers from Network
Another best practice is to segment your backup environment from the rest of the servers and user computers on your network. This provides additional security by limiting the avenues in which an attacker can reach your backup environment. In other words, hiding your backup environment in plain sight.
Fighting Ransomware with Immutable Backups
Immutable backups are the next evolution of backup security to help keep your data safe by preventing the deletion or manipulation of backup data. In other words, immutable backups make it so that once a backup is created it's fixed and locked. With immutable backups, even if an attacker were able to gain access to the backup storage repository your files are protected from deletion. This not only helps in the event of a ransomware attack where there was nefarious intent to cause harm to your company but can also help protect your data in the event of accidental deletion. Since immutable backups introduce a 30-day hold period prior to the data being dumped, you reduce the risk of permanent data loss.
An additional option that comes with the immutability of backups is that it ensures any data that is set to be deleted follows a defined retention policy regarding Delayed Delete Requests. If data needs to be deleted outside (or before) your retention schedule, settings can be configured to require multiple users to log in and delete the data before it is purged completely from your backup storage or device. Think of it like the recycling bin on Windows. You technically "delete" the data, but it doesn't go away immediately. The best practice is to configure Delayed Delete Requests to roughly 10 days, as that would cover most any vacation situation.
In the end, immutable backups help increase the integrity and availability sides of the CIA triad by making backed up data and confidential information both accessible and unchangeable once written to a storage device.
Looking to deploy a secure by default Backup and Disaster Recovery strategy to strengthen data protection and reduce revenue and productivity loss in the event of a ransomware attack? Take the first step in fortifying your data protection by contacting Centre Technologies.




