The State of Cybersecurity in Healthcare
Intel recently announced the results of a security readiness assessment identifying overall security maturity priorities, readiness, gaps and opportunities for improvement that collected actual metrics from over 40 participating HLS Industry Partners last February (2017).
Now one year later in 2018, over 140 HLS organizations are participating in this assessment to find out where weaknesses lie specifically in their own organizations and among the healthcare industry as a whole. The program assessed an organizations security maturity in 42 key security areas and categorizes the controls into three distinct groups:
1. Baseline
This area represents security controls that are considered basic security controls and implemented by most HLS organizations, including:
- Governance (Policies and Procedures)
- Risk Assessments
- Security Awareness Training
- Anti-Malware
- IAM
- Basic Network Defenses
- Incident Response
- Secure Disposal of ePHI
- Backups and Restore Operations
2. Enhanced
This area of controls is considered as enhanced, including:
- Vulnerability Scans
- Pen Tests
- FDE
- DLP
- Remote Wipe
- Secure Remote Access
- MFA
- Endpoint Detection and Response
- Encryption At Rest
- Network Segmentation
- BAAs
- Hypervisor Environment
- Network Intrusion Prevention
3. Advanced
The controls in this area are considered advanced but no less critical, including:
- Network DLP
- FDE using SSD
- Database Activity Monitoring
- Forensics
- SIEM or Cyber-SOC MDR
- Threat Intel
- MFA Whitelisting
- De-Identification
- Tokenization
- Continuity and Resiliency (DRP and BCP)
The Downside of Treating the Symptoms—and Not the Patient
But of particular interest to us at Centre and our partners the identified low implementation rates for many of these types of controls among the industry as shown in the table below. Many of these controls which have now become critical because of the evolving threat environment are offered by Centre through our vetted C-Stack solutions and Partners.
"One critical error business's make when architecting their security solution is the lack of continued managment of vulnerabilities. In this fast paced and ever changing landscape of cyber war, your livelyhood hinges on proactively and continuosly improving your security posture through total network visibility and vulnerability management." —Security Engineer
Below are the Global Stats as of February 2017…Stay tuned for more on this year’s report not yet released. Poor scores highlighted in yellow and red are where Centre Technologies and our C-stack solutions can help close the security gaps.
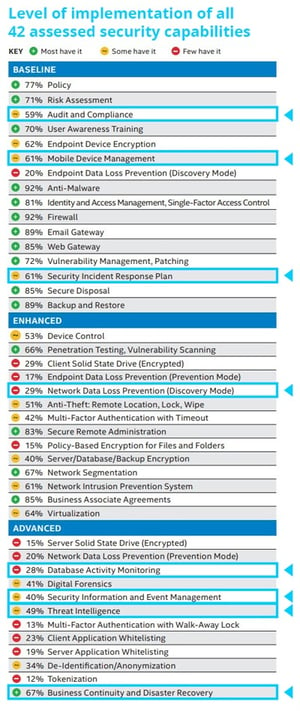
Figure 1 - Level of implementation of all 42 assessed security capabilities from page 4 of the Intel's Whitepaper on Healthcare Security Readiness - Global Industry Highlights
First Step to Better Security Posture
Centre has partnered with Check Point who offers the ability to receive FREE security mapping of your network through an on-site security check-up. This check-up in non-invasive to your network and provides full visibility of your network, resulting in a detailed Security CheckUp Threat Analysis Report. Check Point has 25 years of demonstrated information security products and offers security solutions capable of meeting NIST 800-53-High-Impact standards in both on-premise and cloud environments.
To Build or to Buy?
IT professionals across all industries are expected to bring their "A" game everyday. And you deliver better results for your organization when you are able to focus on evolving technology as a whole.
Don't allow the constant deluge of security alerts douse your flame. You wouldn't ask your ace pitcher to hit a home run, so why should you be expected to manage security when your team is busy maintaining your network? Our partner Arctic Wolf Networks provides SOC-as-a-Service—allowing you to get back to performing like the IT all-star you are.
Contact us today for additional information or if you would like help in conducting a similar more focused assessment of your own environment.




