Avoid Microsoft Azure OMI Vulnerability with Operational Intelligence
OMIGOD is just the latest Microsoft Azure vulnerability to hit the news. Initial estimation is thousands of Azure customers and millions of affected endpoints by what is being commonly referred to as “OMIGOD” zero-days, named after the reaction upon discovery of the open source vulnerability. Many Azure customers are unknowingly at risk. There's always a race amongst botnets to see who can compromise hosts first, but Operational Intelligence for Microsoft Azure can help.
The OMIGOD vulnerability stems from automatic "on-by-default" Azure agent installs on Linux Virtual Machines (VM) that inherently introduces multiple vulnerabilities into your environment. A software agent known as Open Management Infrastructure (OMI) is embedded in various Azure services. Unbeknownst to customers, when a Linux VM is setup in an Azure environment the OMI agent is automatically deployed.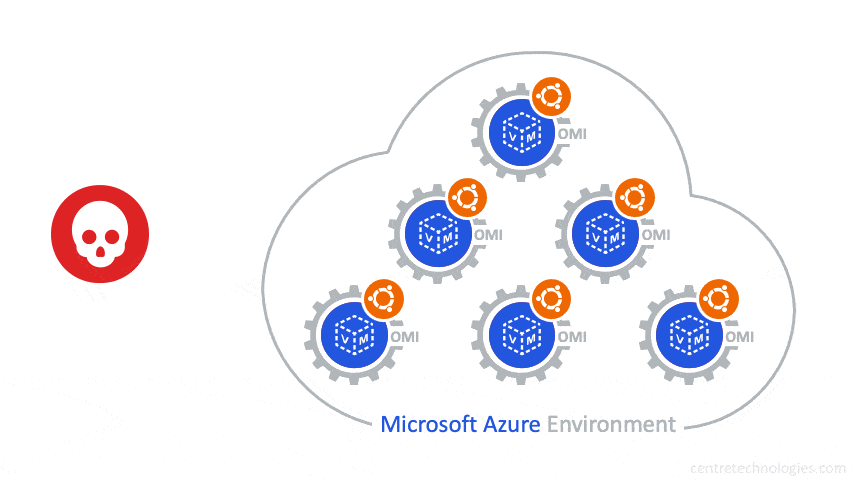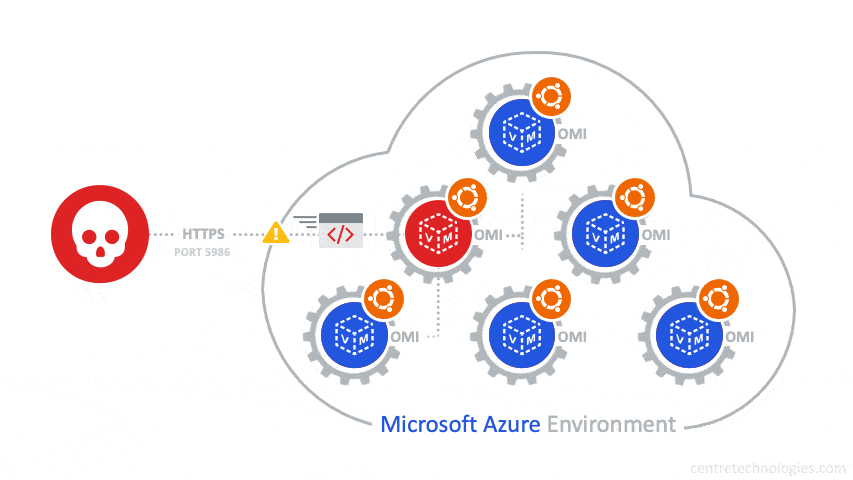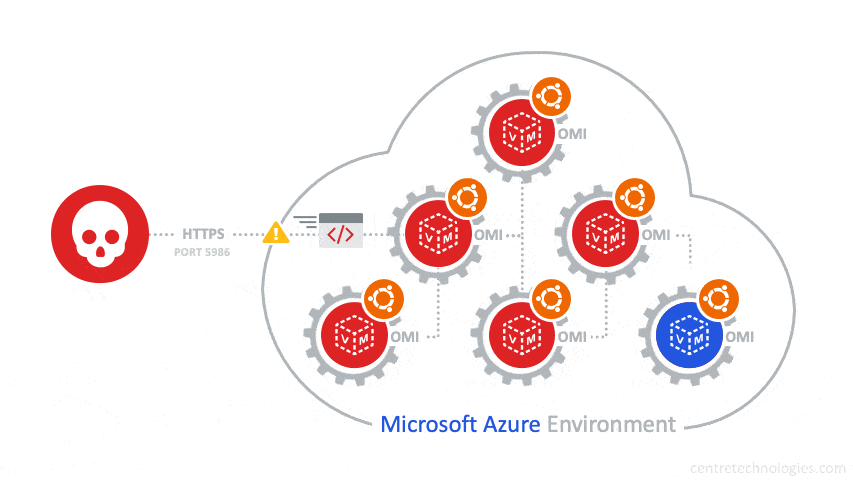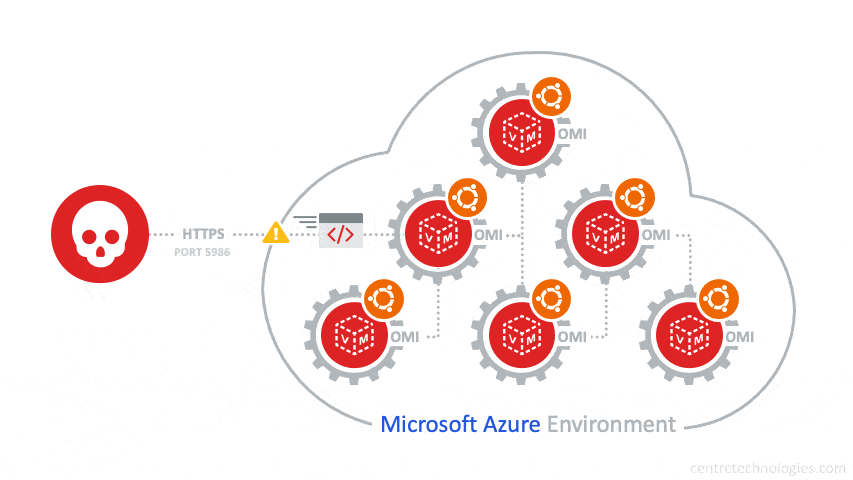
What is OMI and what does it do?
Many businesses have chosen to migrate traditional on-prem computing to Microsoft Azure cloud-based services to accelerate and scale business operations and productivity. OMI is an open source tool designed for monitoring purposes, helping gather statistics and sync configurations across a Microsoft Azure environment. It’s essentially Windows Management Interface (WMI) for Unix/Linux systems. OMI agents enable many common built-in Azure services, including:
- Automation
- Configuration Management
- Diagnostics
- Log Analytics
- Operations Management Suite (OMS)
Since the OMI agent runs as root with the highest privileges, vulnerabilities like OMIGOD and alike can exploit external or low-privileged users in order to execute code on target machines—and even escalate privileges. Additionally, some services like Microsoft Azure Configuration Management exposes an HTTPS port when running OMI services, specifically port 5986, thus enabling a Remote Code Execution (RCE) exploit.
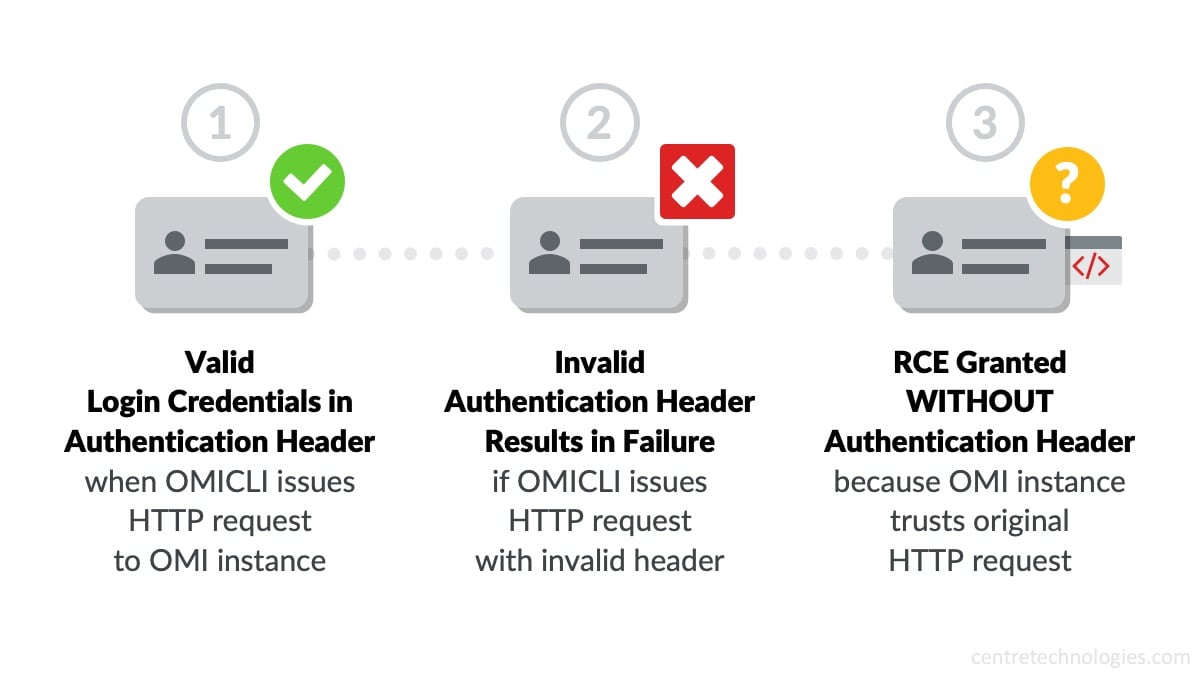
Source: "OMIGOD: Critical Vulnerabilities in OMI Affecting Countless Azure Customers" by Wiz.io
System Administrators of Linux systems hosted on Azure can see if OMI is running in their environment by monitoring ports on TCP 5985 and 5986. Respectively, if your deployments are handled in Microsoft System Center, instead of Azure, then listen to ports on TCP 1270. Even in the case that you have a Unix socket without the mentioned ports, the vulnerability of potential escalated privileges may still be present.
All is not lost, as Microsoft issued four CVEs for OMIGOD and made a patch available to customers during their September 2021 Patch Tuesday release.
How Operational Intelligence helps combat Vulnerabilities like OMIGOD
The OMIGOD vulnerability stems from using open source agents for monitoring. One way to reduce the likelihood of being exported by OMI vulnerabilities is to leverage monitoring services that don't use open source agents. Centre Technologies offers a Microsoft Azure Operational Intelligence package that includes monitoring that uses an agent-less approach. No agent is deployed that can potentially get compromised.
Furthermore, Centre certified Microsoft cloud experts configure exposed ports to be blocked as part of Centre's secure by default migration process standards and deploy agent-less monitoring tools as part of the Operational Intelligence deployment.
Adding Operational Intelligence to your Microsoft Azure environment not only removes the potential risks associated with "on-by-default" open source agents, but also maximizes your cloud advantage in Azure with:
- Comprehensive Cloud Infrastructure Reports and Executive Summaries
- CMAC™ Dashboard (Centre Metrics Assurance and Compliance)
- 24x7 "Always-on" Performance Monitoring
- Efficiency and Security Intelligence
- Application, Usage, and Network Connectivity Metrics
- Backup Recovery Verification
- Access to Certified Cloud Solutions Experts
- Secure by Default IT Blueprint™ for cloud adoption and compliance
While vulnerabilities like OMIGOD will never fully go away, there are cloud solutions available to avoid falling victim to similar exploits. Leveraging a local Microsoft Cloud Solution Provider like Centre Technologies opens the door to not only overcome the disadvantages of cloud computing, but maximize your cloud advantage at the same time.




